H3C MER8300(固定外IP) 为 中心节点,用策略模板模式,连接各地设备(动态外网IP,动态内网IP(多次NAT),固定外网IP)做ipsec vpn (有TPLINK、H3C 5200、 H3C ER8300G2-X、HW AR110-S)
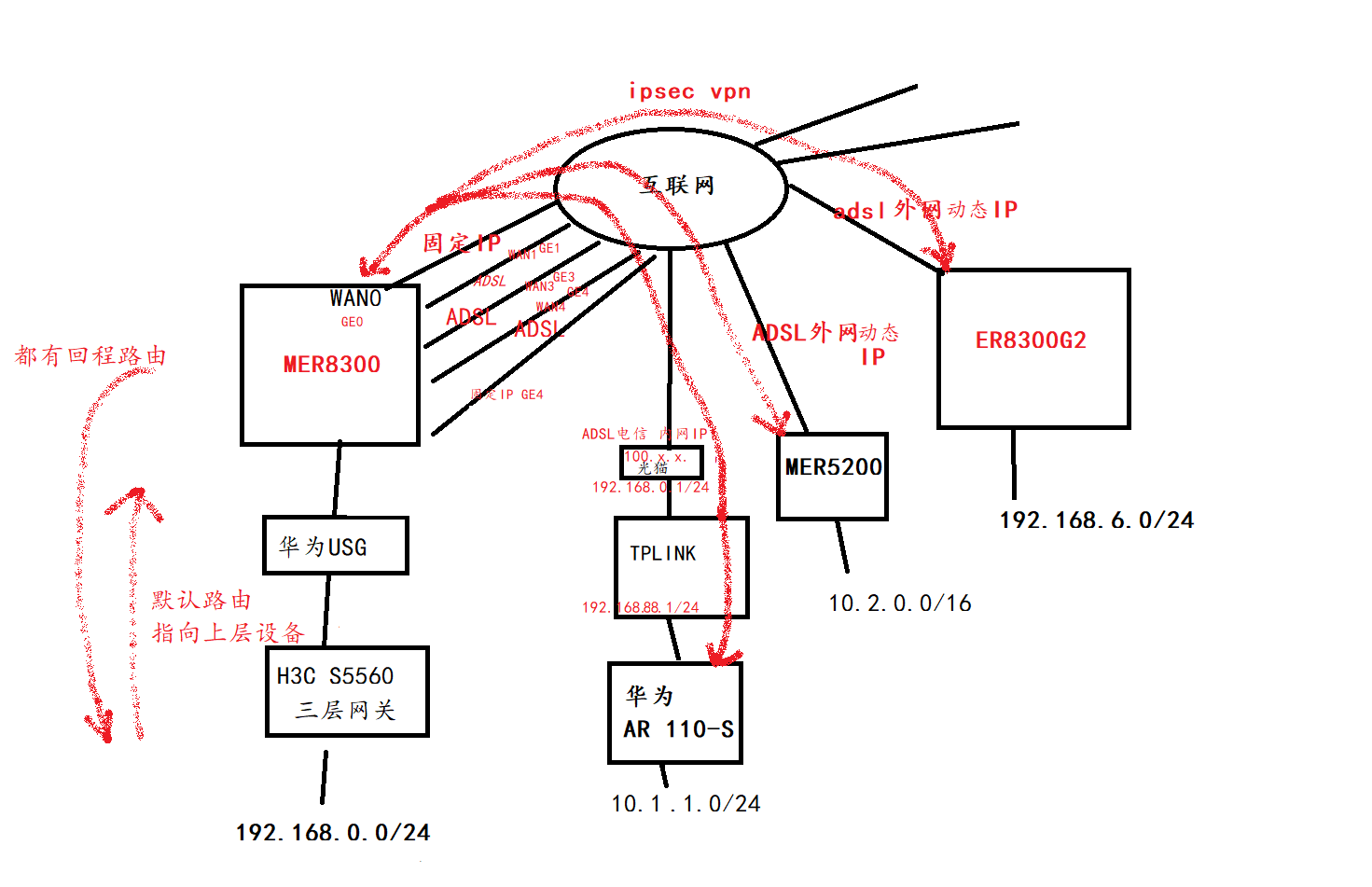
一、中心节点原本为H3C ER8300G2-X,
优点,纯WEB配置,简单可靠,负载均衡后的端口可以选不参与流量(从而不干涉ipsec vpn流量)
缺点:不支持命令配置(链路汇聚),并且IPSEC VPN隧道有限,包转发能力也有限
选中了较为入门、级别高一些,支持命令的MER8300,过程WEB搭建时,垃圾得一塌糊涂,很多功能都必须命令来配置,为什么华为就没这个问题? 下次就应该买华为的设备了。
二、MER8300 配置ipsec vpn
1、一开始用MER8300 WEB配置,ipsec死活就是存在问题,ssh后用命令查看 dis ike sa、dis ipsec sa 、dis ip rou 目的ip、debug 一些列查询后
发现E0口做的ipsec vpn,会收到几个负载均衡口的影响,从而造成ipsec 对端来的包正常,出去的包异常,从dial1或者dial2或者dial3去了,
通过策略路由做ipsec 源地址,目的地址指向E0口
同时,发现MER5200的WEB也是坑爹货,设置后,发现各种命令失却的,例如本端身份类型 FQDN,WEB配置后,命令里面是没有的,需要自己手动打上 local-identity xxxx,否则对端WEB中心节点配置,会无法匹配FQDN,
2、通过命令手册,配置策略模板,把相关配置补全,同样也是存在这个负载的问题
三、MER8300配置本地策略路由,并在LAN口引用
policy-based-route pbr17413 permit node 2
if-match acl name acl174132
apply next-hop E0口网关IP
//把去往ipsec对端的内网IP加入acl进行匹配,对端有多少条就加多少条,可以从WEB加,但就不能通过node 调整优先级了
interface Vlan-interface1
ip policy-based-route pbr17413
//LAN口引用
ip local policy-based-route pbr
policy-based-route pbr permit node 10
if-match acl 3500
apply next-hop E0口网关IP
acl advanced 3500
rule 20 permit ip source E0口IP 0
//本地引用策略
interface GigabitEthernet0/0
ip last-hop hold
nat outbound 3100
ipsec apply policy WAN0(GE0)
ipsec no-nat-process enable //这条不加也行,反正nat兴趣流已经生效,但这条官网说明是nat没有屏蔽兴趣流时,用这条是可以减轻nat压力,有时间切回去尝试看看
ipsec transform-set WAN0(GE0)@all_branches
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group1 //故意跟分支模式分开,这里用DH1,分支模式用DH2
#
ipsec transform-set WAN0(GE0)@branches_a
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2 //故意跟中心模式分开,分支模式用DH2
#
ipsec policy-template WAN0(GE0) 900
transform-set WAN0(GE0)@branches_a
local-address E0口IP
remote-address 对端IP
description WAN0(GE0)@branches_a
ike-profile WAN0(GE0)@branches_a
sa duration time-based 3600
sa duration traffic-based 1843200
reverse-route dynamic
reverse-route preference 50
//对端是固定IP的,分支模式,WEB无法配置多条ipsec策略,我们用命令来实现
#
ipsec policy-template WAN0(GE0) 1000
transform-set WAN0(GE0)@all_branches
description WAN0(GE0)@all_branches
ike-profile WAN0(GE0)@all_branches
sa duration time-based 3600
sa duration traffic-based 1843200
reverse-route dynamic
reverse-route preference 50
//对端动态IP,中心模式
#
ipsec policy WAN0(GE0) 900 isakmp template WAN0(GE0)
#
ipsec policy WAN0(GE0) 1000 isakmp template WAN0(GE0)
#
ike profile WAN0(GE0)@all_branches
keychain WAN0(GE0)@all_branches
dpd interval 30 on-demand
exchange-mode aggressive
local-identity fqdn all.com
match remote identity address 0.0.0.0 0.0.0.0
match remote identity fqdn a.com
match remote identity fqdn b.com
match remote identity fqdn c.com //WEB无法配置多条,对端有多少加多少
proposal 1000
#
ike profile WAN0(GE0)@branches_a
keychain WAN0(GE0)@branches_a
dpd interval 30 on-demand
match remote identity address 对端IP 255.255.255.255 //对方固定IP
proposal 1000
#
ike proposal 1000
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain WAN0(GE0)@all_branches
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher simple123
#
ike keychain WAN0(GE0)@branches_a
pre-shared-key address 对方固定IP 255.255.255.255 key simple abc
#
三、MER5200配置,需手动加入FQDN
ipsec transform-set WAN0(GE0)@a_all
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group1
#
ipsec policy WAN0(GE0) 20748 isakmp
transform-set WAN0(GE0)@a_all
security acl name WAN0(GE0)a_all
remote-address "MER8300 E0口IP"
description WAN0(GE0)@a_all
ike-profile WAN0(GE0)@a_all
sa trigger-mode auto
sa duration time-based 3600
sa duration traffic-based 1843200
#
ike profile WAN0(GE0)@a_all
keychain WAN0(GE0)@a_all
dpd interval 30 on-demand
exchange-mode aggressive
local-identity fqdn a.com
match remote identity fqdn all.com
proposal 20748
#
ike proposal 20748
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain WAN0(GE0)@a_all
pre-shared-key address 0.0.0.0 0.0.0.0 key simple abc123
interface Dialer0
nat outbound 3100
//拨号口取消原有nat outbound,重新配置调用acl,屏蔽兴趣流nat
acl number 3100
description no-nat-ipsecvpn
rule 2000 deny ip source 10.2.0.0 0.0.255.255 destination 192.168.0.0 0.0.0.255
rule 60000 permit ip
//用于屏蔽兴趣流nat
acl advanced name WAN0(GE0)@a_all
rule 0 permit ip source 10.1.1.0 0.0.255.255 destination 192.168.0.0 0.0.0.255
//兴趣流
四、华为ar110-s
命令有点变化,但跟MER5200原理一样。
ipsec proposal b_a
esp authentication-algorithm md5
esp encryption-algorithm 3des
ike proposal 1
encryption-algorithm 3des
dh group2
authentication-algorithm md5
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer b_a
undo version 2
exchange-mode aggressive
pre-shared-key simple abc123
ike-proposal 1
local-id-type fqdn //手动配置
remote-id-type fqdn //手动配置
remote-id all.com
local-id b.com
dpd type periodic
remote-address "MER8300 E0口IP"
rsa encryption-padding oaep
rsa signature-padding pss
ikev2 authentication sign-hash md5
#
ipsec policy b_a 2000 isakmp
security acl 3999
pfs dh-group1
ike-peer b_a
proposal b_a
route inject dynamic
acl number 3000
rule 5 deny ip source 10.1.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 10 permit ip source 10.1.1.0 0.0.0.255
acl name b_a 3999
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
interface GigabitEthernet0/0/4
nat outbound 3000 //WAN口引用nat 屏蔽兴趣流nat
ipsec policy b_a //引用ipsec 策略
五、总结
MER8300配置后,无法从内网访问外网口的管理端口,这个跟ER8300G2-X一样,不过NAT到内网的端口映射正常访问,这个问题就不纠结了,从内网访问LAN口VLAN1 的IP即可。
H3C低端设备的WEB做得实在垃圾,我感觉高端也差不多,还不如ER8300G2-X这种傻瓜路由啊!
华为ar110-s低端的WEB也是存在类似这个问题,功能不全。
H3C的防火墙ipsec vpn没配置过,华为的USG防火墙网页配置ipsecvpn很完善直观也没问题。
再而是TPLINK、傻瓜R8300G2-X的WEB配置IPSECVPN非常直观和简单,以前用过360网神,网康,飞塔,软件防火墙pfsense、openwrt等等WEB配置都非常简单,功能也很完善。
还是命令直观啊。
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4732.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~