我们知道在企业网络中当网络设备众多的时候,我们通常会选择用LLDB的方式查看邻居关系,从而很好的知道相应的邻居关系。
[CORE]display lldp neighbor-information list //查看所有的邻居
Chassis ID : * -- -- Nearest nontpmr bridge neighbor
# -- -- Nearest customer bridge neighbor
Default -- -- Nearest bridge neighbor
System Name Local Interface Chassis ID Port I D
H3C XGE1/0/49 86c4-4d04-0200 Ten-Gi gabitEthernet1/0/49
H3C XGE1/0/50 86c4-7935-0300 Ten-Gi gabitEthernet1/0/49
----------------------------------------------------------------------------------------
[CORE]display lldp neighbor-information interface Ten-Gigab itEthernet 1/0/49 //查看XG1/0/49端口的邻居
LLDP neighbor-information of port 50[Ten-GigabitEthernet1/0 /49]:
LLDP agent nearest-bridge:
LLDP neighbor index : 1
ChassisID/subtype : 86c4-4d04-0200/MAC address
PortID/subtype : Ten-GigabitEthernet1/0/49/Interface name
Capabilities : Bridge, Router, Customer Bridge
[CORE]
我们通过下面的简单拓补,来看看如何根据端口配置信息来判断某台交换机的周围还可能有什么设备。
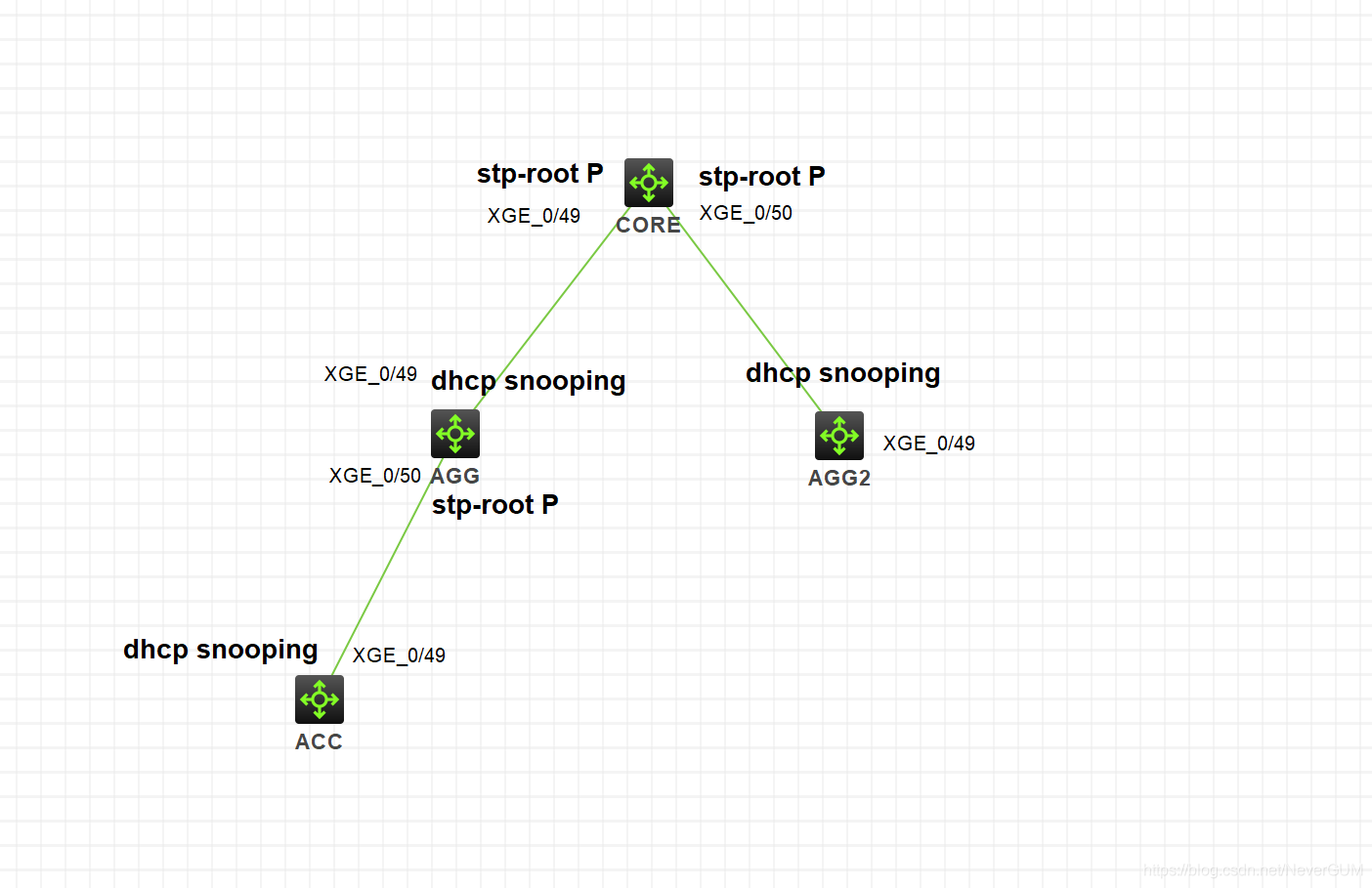
看下配置:
CORE
[H3C]sysname CORE
[CORE]dhcp enable
[CORE]interface Vlan-interface 1
[CORE-Vlan-interface1]ip address 192.168.1.254 24
[CORE-Vlan-interface1]quit
[CORE]dhcp server ip-pool test
[CORE-dhcp-pool-test]network 192.168.1.0 mask 255.255.255.0
[CORE-dhcp-pool-test]gateway-list 192.168.1.254
[CORE-dhcp-pool-test]dns-list 114.114.114.114
[CORE-dhcp-pool-test]
[CORE]stp mode rstp
[CORE]interface range Ten-GigabitEthernet 1/0/49 to Ten-GigabitEthernet 1/0/50
[CORE-if-range]stp root-protection
[CORE-if-range]
//由于端口被设定了根保护,根据STP的选举原理,49,50端口成为了指定端口
[CORE]display stp brief
MST ID Port Role STP Sta te Protection
0 Ten-GigabitEthernet1/0/49 DESI FORWARD ING NONE
0 Ten-GigabitEthernet1/0/50 DESI FORWARD ING NONE
[CORE]
AGG
<H3C>sy
<H3C>system-view
System View: return to User View with Ctrl+Z.
[H3C]un
[H3C]undo inf en
Information center is disabled.
[H3C]sys AGG
[AGG]dhcp enable
[AGG]interface Ten-GigabitEthernet1/0/49
[AGG-Ten-GigabitEthernet1/0/49]dhcp snooping trust
[AGG-Ten-GigabitEthernet1/0/49]quit
[AGG]interface Vlan-interface 1 //我们采用dhcp-alloc的方式让vlanif1获取一个IP地址
[AGG-Vlan-interface1]ip address dhcp-alloc
[AGG-Vlan-interface1]quit
[AGG]
[AGG]display interface Vlan-interface brief //此时我们看到vlan1获取到了地址,192.168.1.2
Brief information on interfaces in route mode:
Link: ADM - administratively down; Stby - standby
Protocol: (s) - spoofing
Interface Link Protocol Primary IP Description
Vlan1 UP UP 192.168.1.2
[AGG]
一:我们想知道这台设备连了哪些交换机,它的定位是上联还是下联设备。
1:首先,我们用dis cur 查看配置,在核心交换机上发现了,G1/0/49 和G1/0/50端口被配置了stp root-protection,由于配置了根保护,跟保护的意义就在于为了保证下联网络设备到此端口的路径是最优的,所以,这个端口看到是某个交换机设备的上联端口,我们则可以用,display lldp neighbor-information interface Ten-GigabitEthernet 1/0/49 verbose的命令,查看本端口连了什么设备,甚至对方的IP地址都可以看的出来。
[CORE]display lldp neighbor-information interface Ten-GigabitEthernet 1/0/49 verbose
LLDP neighbor-information of port 50[Ten-GigabitEthernet1/0/49]:
LLDP agent nearest-bridge:
LLDP neighbor index : 1
Update time : 0 days, 0 hours, 37 minutes, 3 seconds
Chassis type : MAC address
Chassis ID : 86c4-4d04-0200
Port ID type : Interface name
Port ID : Ten-GigabitEthernet1/0/49
Time to live : 121
Port description : Ten-GigabitEthernet1/0/49 Interface
System name : AGG
System description : H3C Comware Platform Software, Software Version 7.1.075,
Alpha 7571
H3C S5820V2-54QS-GE
Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. Al
l rights reserved.
System capabilities supported : Bridge, Router, Customer Bridge, Service Bridge
System capabilities enabled : Bridge, Router, Customer Bridge
Management address type : IPv4
Management address : 192.168.1.2
Management address interface type : IfIndex
Management address interface ID : 1412
Management address OID : 0
Port VLAN ID(PVID) : 1
Link aggregation supported : Yes
Link aggregation enabled : No
Aggregation port ID : 0
Auto-negotiation supported : No
Auto-negotiation enabled : No
OperMau : Speed(0)/Duplex(Unknown)
Power port class : PSE
PSE power supported : No
PSE power enabled : No
PSE pairs control ability : No
Power pairs : Signal
Port power classification : Class 0
Maximum frame size : 9216
[CORE]
2:我们看第二个交换机,AGG,我们发现该端口设置了dhcp-snooping trust ,那么设置了此条命令,意味着该G1/0/49端口一定是某个交换机的下联设备,因为设置dhcp-snooping trust的意义就是防止客户端获取了非法DHCP服务器的IP,造成一定的安全隐患。设置了此信任端口,那么此交换机的其他端口就会默认变成untrust(非信任)端口,针对用户私接小路由器特别有效果。
[AGG]display current-configuration interface Ten-GigabitEthernet 1/0/49
#
interface Ten-GigabitEthernet1/0/49
port link-mode bridge
combo enable fiber
dhcp snooping trust
#
return
[AGG]
看到此端口的配置,那么我们可以肯定的是,这台设备上面肯定还有一台设备,而且它还是此端口所在设备的上联网络设备,我们再使用查看邻居接口的方法 ,此端口对端的设备信息被我们看的清清楚楚。
//管理IP
//对端所在端口
...等等一系列信息。
[AGG]display lldp neighbor-information interface Ten-GigabitEthernet 1/0/49 verb
ose
LLDP neighbor-information of port 50[Ten-GigabitEthernet1/0/49]:
LLDP agent nearest-bridge:
LLDP neighbor index : 1
Update time : 0 days, 0 hours, 36 minutes, 30 seconds
Chassis type : MAC address
Chassis ID : 86c4-3be4-0100
Port ID type : Interface name
Port ID : Ten-GigabitEthernet1/0/49
Time to live : 121
Port description : Ten-GigabitEthernet1/0/49 Interface
System name : CORE
System description : H3C Comware Platform Software, Software Version 7.1.075,
Alpha 7571
H3C S5820V2-54QS-GE
Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. Al
l rights reserved.
System capabilities supported : Bridge, Router, Customer Bridge, Service Bridge
System capabilities enabled : Bridge, Router, Customer Bridge
Management address type : IPv4
Management address : 192.168.1.254
Management address interface type : IfIndex
Management address interface ID : 1412
Management address OID : 0
Port VLAN ID(PVID) : 1
Link aggregation supported : Yes
Link aggregation enabled : No
Aggregation port ID : 0
Auto-negotiation supported : No
Auto-negotiation enabled : No
OperMau : Speed(0)/Duplex(Unknown)
Power port class : PSE
PSE power supported : No
PSE power enabled : No
PSE pairs control ability : No
Power pairs : Signal
Port power classification : Class 0
Maximum frame size : 9216
实验成果
//某个端口如果被配置了stp root-protection ,那么这个端口所在的交换机一定是某个交换机的上联网络设备。
stp root-protection命令用来使能当前端口的根保护功能。
应用场景
由于维护人员的错误配置或网络中的恶意攻击,根桥收到优先级更高的BPDU,会失去根桥的地位,重新进行生成树的计算。由于拓扑结构的变化,可能造成高速流量迁移到低速链路上,引起网络拥塞。
对于使能根保护功能的指定端口,其端口角色只能保持为指定端口。一旦使能根保护功能的指定端口收到优先级更高的BPDU时,端口状态将进入Discarding状态,不再转发报文。在经过一段时间(通常为两倍的Forward Delay),如果端口一直没有再收到优先级较高的BPDU,端口会自动恢复到正常的Forwarding状态。
所以企业网络中,一般会在下联其他设备端口配置根保护,使得端口角色保持为指定端口
//某个端口如果被配置了dhcp-snooping trust,那么这个端口所在的交换机一定是某个交换机的下联网络设备。
结语
事实上,配置规范的网络设备通常能给后期运维带来很多好处,甚至安全方面也有举足轻重的效果。
//设备命名,时间配置,掉线时间,描述信息,
//根保护,dhcp snooping,lldb,SNMP ,acl等等 。。。。。
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/2332.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~