华为USG AD域认证,按手册配置,测试用户时, 提示: AD票据授权失败。
debug 日志提示: check tag 2 err, may don't have tag 2.
AD票据授权失败有多种原因,请参考下面两个链接中的方法处理下吧。
https://support.huawei.com/hedex/hdx.do?docid=EDOC1000160161&id=ZH-CN_TOPIC_0105396312&lang=zh
https://support.huawei.com/hedex/hdx.do?docid=EDOC1000160161&id=ZH-CN_TOPIC_0105482498&lang=zh
根据 debug 日志提示: check tag 2 err, may don't have tag 2. 下面的处理方法可以解决问题。
https://support.huawei.com/enterprise/zh/knowledge/EKB1100068766
Issue Description
USG Firewall failed to communicate with AD server
Handling Process
[1] Check the software version V600R007C00SPC20
===================================================
===============display version===============
===================================================
2021-03-05 12:49:30.120 +05:00
Huawei Versatile Routing Platform Software
VRP (R) Software, Version 5.170 (USG6600E V600R007C00SPC200)
Copyright (C) 2014-2019 Huawei Technologies Co., Ltd.
USG6615E uptime is 0 week, 3 days, 16 hours, 12 minutes
[2] check the failed reason as below
In V500R005C20SPC500 and V600R007C00SPC200 and their later versions, LDAP over SSL is used for LDAP authentication between the device and AD server by default for security purposes. The device uses the CA certificate to authenticate the AD server. When a device is upgraded from an earlier version to V500R005C20SPC500 or V600R007C00SPC200 or a later version, or a device running V500R005C20SPC500 or V600R007C00SPC200 or a later version is directly used, check whether LDAP over SSL is enabled on the AD server. If not, run commands on the device to change the protocol used for interaction between the device and AD server to no-ssl.Suggestions
USG 授权认证为Active Directory的问题总结
一、试验环境
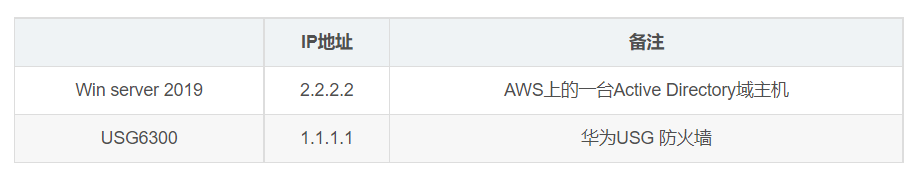
IP地址 备注
Win server 2019 2.2.2.2 AWS上的一台Active Directory域主机
USG6300 1.1.1.1 华为USG 防火墙
以上IP地址1.1.1.1和2.2.2.2并非真实环境中的公网IP地址
二、前提
1、USG和Active Directory域的主机之间可以ping通
2、Active Directory域主机的安全组放通了88和389端口
3、Active Directory域主机也关闭了本地防火墙
4、Active Directory域主机的安全组放通了USG防火墙所在的公网ip地址段
5、PC上telnet Active Directory域主机的2.2.2.2:88,2.2.2.2:389可以通
三、故障现象
1、防火墙上telnet -a 1.1.1.1 2.2.2.2 88 不通
2、防火墙上telnet -a 1.1.1.1 2.2.2.2 389 不通
3、使用kangbao.wu 账号进行验证,报错为:Active Directory票据授权失败
4、使用kangbao.it账号进行验证,报错为:Active Directory管理员绑定失败
四、排查思路
针对"防火墙上telnet -a 1.1.1.1 2.2.2.2 88 不通"
针对"防火墙上telnet -a 1.1.1.1 2.2.2.2 389 不通"
1、查看Active Directory域安全组和防火墙是否放通了地址和接口---->全部放通
2、查看USG防火墙的域间策略是否配置正确---->默认全部放通
我没辙了,居然内心想来一句"卧槽",
然后我拨打了华为400,结果告知我 华为的网络设备除了22 23端口可用于telnet 测试,其他的端口不能通过telnet ip:port这种测试端口可用性
针对"使用kangbao.wu 账号进行验证,报错为:Active Directory票据授权失败"
针对"使用kangbao.it账号进行验证,报错为:Active Directory管理员绑定失败"
配置如下:
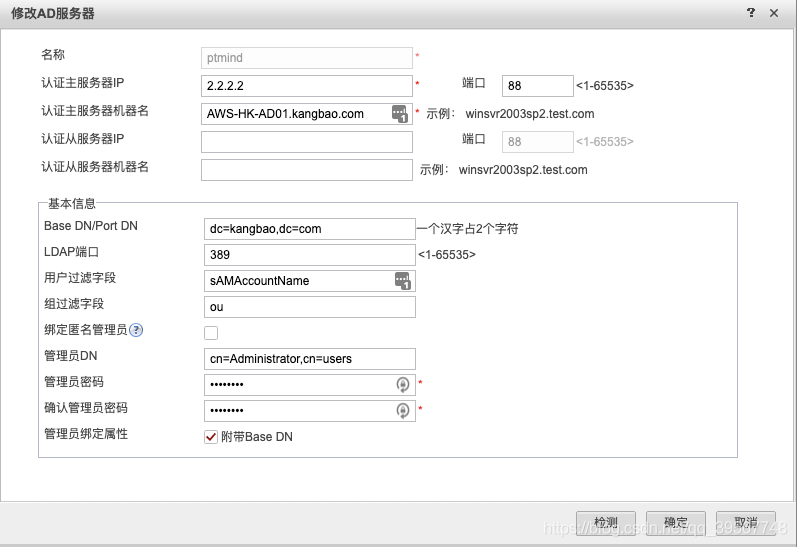
通过在USG防火墙上查看
t m
t d
debugging ad all
Jan 14 2020 10:43:06.940.2+08:00 Office_vpn AD/7/debug:[AD(Evt):] Initialize AD server to primary.
Jan 14 2020 10:43:06.940.3+08:00 Office_vpn AD/7/debug:[AD(pkt):] Make UDP kerbores AS Request packet successfully,username: kangbao.wu
Jan 14 2020 10:43:06.940.4+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send packet to AD-server(ServerIP:18.162.178.138,Port:88)
Jan 14 2020 10:43:06.940.5+08:00 Office_vpn AD/7/debug:send ad UDP packet success :228
Jan 14 2020 10:43:06.940.6+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send UDP kerbores AS request packet successfully.
Jan 14 2020 10:43:07.60.1+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Recevied kerbores packet successfully, username: kangbao.wu.
Jan 14 2020 10:43:07.60.2+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Kerberos server's response is bad, ErrorCode: 24.
Jan 14 2020 10:43:07.60.3+08:00 Office_vpn AD/7/debug:[AD(Err):] Kerberos server's response is bad, ErrorCode: 24.
Jan 14 2020 10:43:07.60.4+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Pre-authentication information was invalid.
Jan 14 2020 10:43:07.60.5+08:00 Office_vpn AD/7/debug:AS-REP Parse ERROR .error is [24]!
Jan 14 2020 10:43:07.60.6+08:00 Office_vpn AD/7/debug:AS-REP Parse ERROR!
Jan 14 2020 10:43:07.60.7+08:00 Office_vpn AD/7/debug:[AD(Err):] Make kerbores TGS Request packet by UDP failed, so try TCP .username: kangbao.wu
Jan 14 2020 10:43:07.60.8+08:00 Office_vpn AD/7/debug:[AD(Err):] parse server As Response error,but error code is not AD_KRB5_ERROR_REPONSE_TOO_BIG(52)!
Jan 14 2020 10:43:07.60.9+08:00 Office_vpn AD/7/debug:[AD(Evt):] kerbores authenication reject.
Jan 14 2020 10:43:07.60.10+08:00 Office_vpn AD/7/debug: free AD connect success !
<Office_vpn>
Jan 14 2020 10:43:37.290.1+08:00 Office_vpn AD/7/debug:[AD(Evt):] Initialize AD server to primary.
Jan 14 2020 10:43:37.290.2+08:00 Office_vpn AD/7/debug:[AD(pkt):] Make UDP kerbores AS Request packet successfully,username: kangbao.it
Jan 14 2020 10:43:37.290.3+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send packet to AD-server(ServerIP:18.162.178.138,Port:88)
Jan 14 2020 10:43:37.290.4+08:00 Office_vpn AD/7/debug:send ad UDP packet success :226
Jan 14 2020 10:43:37.290.5+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send UDP kerbores AS request packet successfully.
Jan 14 2020 10:43:37.400.1+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Recevied kerbores packet successfully, username: kangbao.it.
Jan 14 2020 10:43:37.400.2+08:00 Office_vpn AD/7/debug:[AD(Pkt):] check tag 2 err, may don't have tag 2.
Jan 14 2020 10:43:37.400.3+08:00 Office_vpn AD/7/debug:AD Make Tgs Req OK!
Jan 14 2020 10:43:37.400.4+08:00 Office_vpn AD/7/debug:[AD(Pkt):] check tag 2 err, may don't have tag 2.
Jan 14 2020 10:43:37.400.5+08:00 Office_vpn AD/7/debug:AD Make Tgs Req OK!
Jan 14 2020 10:43:37.400.6+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Make UDP kerbores TGS Request packet successfully,username: kangbao.it
Jan 14 2020 10:43:37.400.7+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send packet to AD-server(ServerIP:18.162.178.138,Port:88)
Jan 14 2020 10:43:37.400.8+08:00 Office_vpn AD/7/debug:send ad UDP packet success :1331
Jan 14 2020 10:43:37.400.9+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Send kerbores TGS Request packet successfully.
Jan 14 2020 10:43:37.510.1+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Recevied kerbores packet successfully, username: kangbao.it.
Jan 14 2020 10:43:37.510.2+08:00 Office_vpn AD/7/debug:[AD(Pkt):] check tag 2 err, may don't have tag 2.
Jan 14 2020 10:43:37.510.3+08:00 Office_vpn AD/7/debug:[AD(Pkt):] Give the Kerberos Ticket to LDAP for verifying.Length is [1231]
Jan 14 2020 10:43:37.510.4+08:00 Office_vpn AD/7/debug:[AD(Evt):] kerbores authenication accept.
Jan 14 2020 10:43:37.510.5+08:00 Office_vpn AD/7/debug: free AD connect success !
sys
diagnose
display ad statistics error
[Office_vpn-diagnose]display ad statistics error
2020-01-14 10:43:58.630 +08:00
mng-plane:
Server_Down_Err_Static = 0
Server_Unavailable_Err_Static = 0
NoServer_Exist_Err_Static = 0
Memory_Application_Err_Static = 0
Memory_Free_Err_Static = 0
IPC_Message_Translate_Err_Static = 0
Server_Client_Time_Not_Match = 0
Server_Timeout_Err_Static = 0
Make_Pack_Fail_Err_Static = 1
Abnormal_Err_Static = 0
AS_Reject_Err_Static = 0
TS_Reject_Err_Static = 1
APR_Reject_Err_Static = 0
ctrl-plane:
Server_Down_Err_Static = 0
Server_Unavailable_Err_Static = 0
NoServer_Exist_Err_Static = 0
Memory_Application_Err_Static = 0
Memory_Free_Err_Static = 0
IPC_Message_Translate_Err_Static = 0
Server_Client_Time_Not_Match = 0
Server_Timeout_Err_Static = 0
Make_Pack_Fail_Err_Static = 0
Abnormal_Err_Static = 0
AS_Reject_Err_Static = 0
TS_Reject_Err_Static = 0
APR_Reject_Err_Static = 0
1、通过debug信息和ad erro信息得知,Active Directory认证有问题,故进一步排查
2、通过查找资料得知,USG对Active Directory密码有要求,不能有空格和?字符
注意,华为针对Active Directory用户的密码是有要求的,不能有空格和?字符出现,不然就要使用双引号
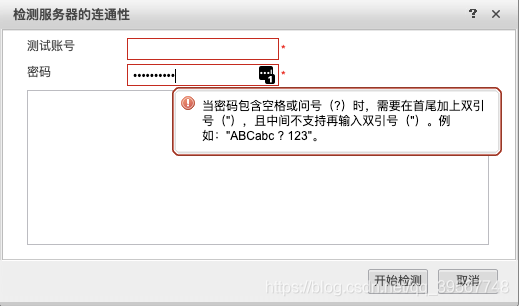
注意,这里并没有说administrator的密码也不可以包含空格和字符,然而我Active Directory的administrator的密码就碰巧有?字符的存在,我萎蔫了
更改了Active Directory域的管理员的密码后,至此,终于解决了所有的问题
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/2504.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~




 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~