###华为 VPN之IPsec(适合一对多)
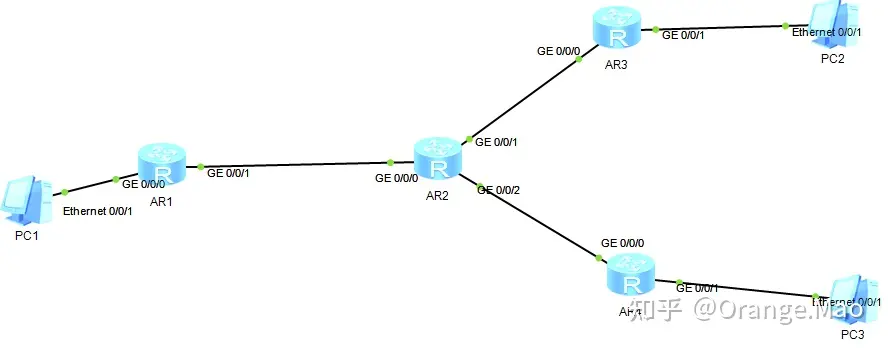
现在自己能做一点对多点了给大家发一下自己写的配置以及拓扑图。大体过程:PC1 :192.168网段,PC2 :167网段,PC3 :166网段;三个都是配置接口DHCP自动获取;路由器AR2配置三个端口地址:10段;12段;13段。
1、创建ACL
[AR1]acl number 3000
[AR1-acl-adv-3000]rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.167.10.0 0.0.0.255 // 匹配需要走VPN的流量
[AR1]acl number 3001
[AR1-acl-adv-3001]rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.166.10.0 0.0.0.255 // 匹配需要走VPN的流量
[AR1]acl number 3002
[AR1-acl-adv-3002]rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.166.10.0 0.0.0.255
[AR1-acl-adv-3002]rule 10 deny ip source 192.168.10.0 0.0.0.255 destination 192.167.10.0 0.0.0.255
[AR1-acl-adv-3002]rule 15 deny ip source 192.168.10.0 0.0.0.255
2、创建IPsec安全提议
[AR1]ipsec proposal 1 // 创建安全提议1(V5平台默认des加密)。与ipsec transform-set命令等效注意默认不加密(V7平台)
[AR1-ipsec-proposal-1]encapsulation-mode tunnel (可略)使用隧道模式,会加上新ip头部,新头部就是两个站点的出口公网地址
[AR1-ipsec-proposal-1]transform esp (可略)封装模式使用esp,因为有加密需求,所以用esp而不是ah
[AR1-ipsec-proposal-1]esp encryption-algorithm aes-256 (可略)加密算法用aes-256
[AR1-ipsec-proposal-1]esp authentication-algorithm sha2-256 (可略)完整性验证算法用sha2-256
[AR1-ipsec-proposal-1]q // 直接退出,用默认设置即可
[AR1]dis ipsec proposal // 可以查看默认设置
3、配置ike(互联网密钥交换协议)
[AR1]ike proposal 1 创建ike提议,编号为1
[AR1-ike-proposal-1]authentication-method pre-share (可略)使用预共享密钥的方式进行身份验证
[AR1-ike-proposal-1]dh group1 (可略)协商密钥的过程,用dh
4、配置对等体
[AR1]ike peer toR3 v1 创建一个对等体,名字为toR3,使用ike
[AR1-ike-peer-toR3]exchange-mode main (可略)使用主模式(main)建立ipsec
[AR1-ike-peer-toR3]pre-shared-key simple maofanghua 预共享密钥,两边一致
[AR1-ike-peer-toR3]ike-proposal 1 调用前面配好的密钥协商方法
[AR1-ike-peer-toR3]remote-address 12.0.0.1 对等体的ip地址,也就是要和这个设备建立ipsec连接
[AR1-ike-peer-toR3]local-address x.x.x.x (可略)本地IP地址
[AR1]ike peer toR4 v1
[AR1-ike-peer-toR4]pre-shared-key simple maofanghua
[AR1-ike-peer-toR4]ike-proposal 1
[AR1-ike-peer-toR4]remote-address 13.0.0.1
——————————————————————————————————————————————————
一个对方固定IP本地动态外网IP,使用IP连接
ike peer A_B
undo version 2
exchange-mode aggressive
pre-shared-key cipher 123456
ike-proposal 3
local-id-type fqdn
remote-id B
local-id A
dpd type periodic
remote-address A_IP
rsa encryption-padding oaep
rsa signature-padding pss
ikev2 authentication sign-hash sha2-256
一个对方固定IP本地动态内网IP,使用FQDN连接 //跟H3C互联隧道成功,但是无法通信
ike peer A_C
undo version 2
exchange-mode aggressive
pre-shared-key cipher 123456
ike-proposal 3
local-id-type fqdn
remote-id-type fqdn
remote-id B
local-id A
dpd type periodic
remote-address B_IP
rsa encryption-padding oaep
rsa signature-padding pss
ikev2 authentication sign-hash sha2-256
——————————————————————————————————————————————————
5、创建ipsec策略
[AR1]ipsec policy vpn 10 isakmp 创建一个ipsec策略,名称是vpn,编号是10
[AR1-ipsec-policy-isakmp-vpn-10]security acl 3000 前面定义的ACL
[AR1-ipsec-policy-isakmp-vpn-10]ike-peer toR3 前面定义好的ipsec对等体
[AR1-ipsec-policy-isakmp-vpn-10]proposal 1 前面定义好的安全提议
[AR1]ipsec policy vpn 11 isakmp
[AR1-ipsec-policy-isakmp-vpn-11]security acl 3001
[AR1-ipsec-policy-isakmp-vpn-11]ike-peer toR4
[AR1-ipsec-policy-isakmp-vpn-11]proposal 1
6、出接口调用
[AR1]interface GigabitEthernet0/0/0
[AR1-GigabitEthernet0/0/0]ip address 192.168.10.254 255.255.255.0
[AR1]interface GigabitEthernet0/0/1
[AR1-GigabitEthernet0/0/1]ip address 10.0.0.1 255.255.255.0
[AR1-GigabitEthernet0/0/1]ipsec policy vpn
[AR1-GigabitEthernet0/0/1]nat outbound 3002
最后,其它路由器参照上述进行配置。结果在192.168.10.x与192.167.10.x与192.166.10.x终端电脑可以相互ping通。但在10与12与13路由上ping192.168.10.x或192.167.10.x或192.166.10.x是不通的,因为ACL没有放行10/12/13的IP。
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4671.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~