配置步骤
1.
interface LoopBack0 # 配置内网接口
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0 # 配置物理接口
ip address 192.168.1.2 255.255.255.0
ipsec apply policy ipsec # 绑定IPSec策略
#
ip route-static 0.0.0.0 0 192.168.1.1 # 配置静态路由
#
acl advanced 3000 # 配置IPSec感兴趣流
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
#
ipsec transform-set ipsec # 配置IPSec转换集
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
#
ipsec policy ipsec 10 isakmp # 配置IPSec策略
transform-set ipsec
security acl 3000
remote-address 200.200.200.2 # 非模板模式必须指定对端地址
ike-profile ike
#
ike identity fqdn vpna # 配置IKE name
#
ike profile ike # 配置IKE对等体
keychain ike
exchange-mode aggressive
match remote identity address 200.200.200.2 255.255.255.255
#
ike keychain ike # 配置IKE预共享密钥
pre-shared-key address 200.200.200.2 255.255.255.255 key simple ipsec
2.
interface LoopBack0 # 配置内网接口
ip address 192.168.3.1 255.255.255.0
#
interface GigabitEthernet0/0 # 配置外网接口
ip address 200.200.200.2 255.255.255.252
ipsec apply policy ipsec # 绑定IPSec策略
#
ip route-static 0.0.0.0 0 200.200.200.1 # 配置静态路由
#
ipsec transform-set ipsec # 配置IPSec转换集
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
#
ipsec policy-template ipsec 10 # 配置IPSec策略模板
transform-set ipsec
ike-profile ike
#
ipsec policy ipsec 10 isakmp template ipsec # 将IPSec策略模板应用到策略中
#
ike profile ike # 配置IKE对等体
keychain ike
exchange-mode aggressive
match remote identity fqdn vpna # 匹配对端name
#
ike keychain ike # 配置IKE预共享密钥
pre-shared-key hostname vpna key simple ipsec
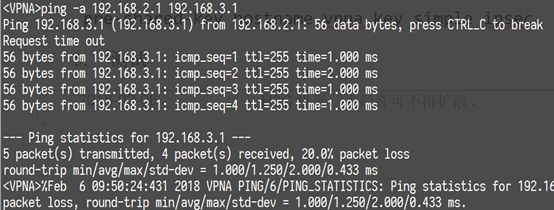
3、测试

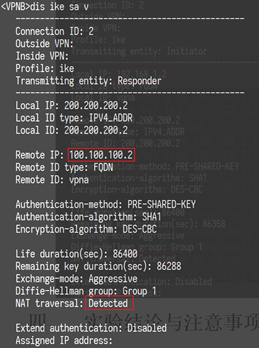
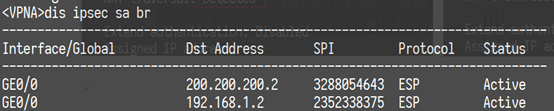
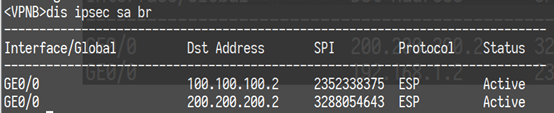
配置关键点
注意模板方式配置的IPSec不能主动触发IPSec SA协商,必须在另一端非模板方式配置的IPSec触发协商。
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4727.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~