IPSec高可靠性技术
IPSec VPN高可靠性概述:
IPSec隧道由网络设备和链路组成,设备故障或者链路故障都会导致IPSec隧道中断,存在单点故障。因此在设计IPSec VPN高可靠性时既要考虑保护链路,也需要考虑保护网络设备。
IPSec高可靠性设计可以分为两类,一种是链路冗余,另一种是主备网络备份。其中链路冗余可以分为主备链路备份和隧道化链路备份。
解决链路单点故障
解决方案概述:
多链路两种思路:
A. 链路的主备方式
2:1模式 2:2 模式
B.隧道化的备份 ----华为建议
通过Tunnel接口进行链路冗余备份可以实现多条链路的冗余备份,而且与主备链路冗余备份相比,配置更简单,流量切换速度更快。
主备链路模式缺点:当主链路DOWN以后切换至备份链路需要重新触发IKE SA IPSEC SA,造成业务中断
隧道备份方式
优点:当物理接口DOWN了,不影响IPSEC隧道的SA,不会影响业务的中断
缺点:隧道接口需要一个公网IP地址。
IPSec 主备链路备份配置示例:
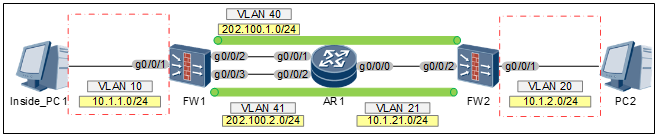
2:1模式的配置思路:
2端 第一步:配置IPSEC VPN 阶段一: ike proposal 10 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256# ike peer fw2 pre-shared-key Huawei@123 ike-proposal 10 remote-address 10.1.21.10阶段二: acl number 3000 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255acl number 3001 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255注意:需要配置两个ACL ipsec proposal 10 esp authentication-algorithm sha2-256ipsec policy map1 10 isakmp security acl 3000 ike-peer fw2 alias map1_10 proposal 10# ipsec policy map2 10 isakmp security acl 3001 ike-peer fw2 alias map2_10 proposal 10 注意:配置两个IPSEC策略对应对方的两个 interface GigabitEthernet0/0/2 ip address 202.100.1.10 255.255.255.0 ipsec policy map1 # interface GigabitEthernet0/0/3 ip address 202.100.2.10 255.255.255.0 ipsec policy map2---------------------------------------------1端 阶段一: ike proposal 10 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256# ike peer a1 pre-shared-key Huawei@123 ike-proposal 10 remote-address 202.100.1.10# ike peer a2 pre-shared-key Huawei@123 ike-proposal 10 remote-address 202.100.2.10注意:需要配置两个PEER,对应不同的物理接口 阶段二: acl number 3000 rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255acl number 3001 rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255注意:需要配置两个感兴趣流 ipsec proposal 10 esp authentication-algorithm sha2-256# ipsec policy map1 10 isakmp security acl 3000 ike-peer a1 alias map1_10 proposal 10# ipsec policy map2 10 isakmp security acl 3001 ike-peer a2 alias map2_10 proposal 10注意:配置两个IPSEC策略interface Tunnel1 ip address unnumbered interface GigabitEthernet0/0/2 tunnel-protocol ipsec ----------隧道协议为IPSEC封装 ipsec policy map1 #interface Tunnel2 ip address unnumbered interface GigabitEthernet0/0/2 tunnel-protocol ipsec ipsec policy map2 第二步:规划路由 主备模式2端 ip route-static 0.0.0.0 0.0.0.0 202.100.2.254 preference 100 ip route-static 0.0.0.0 0.0.0.0 202.100.1.254 1端:需要引导流量进TUNNEL口 ip route-static 10.1.1.0 255.255.255.0 Tunnel2 preference 100 ip route-static 10.1.1.0 255.255.255.0 Tunnel1 第三步:快速切换 配置IP-LINK2端 ip-link check enable ip-link 1 destination 202.100.1.254 interface GigabitEthernet0/0/2 mode icmp ip route-static 0.0.0.0 0.0.0.0 202.100.1.254 track ip-link 1注意:如果不放行安全策略,那IP-LINK就是DOWN的1端 ip-link check enable ip-link 1 destination 202.100.1.254 interface GigabitEthernet0/0/2 mode icmp next-hop 10.1.21.254 ip route-static 10.1.1.0 255.255.255.0 Tunnel1 track ip-link 1第四步:放行安全策略 security-policy rule name IPSEC1 -----------放行建立IPSEC隧道(isakmp和ESP) source-zone local source-zone untrust destination-zone local destination-zone untrust source-address address-set IPSEC1 destination-address address-set IPSEC1 service ISAKMP service esp action permit rule name IPSEC2 --------------放行实际通信流量(感兴趣) source-zone trust source-zone untrust destination-zone trust destination-zone untrust source-address address-set IPSEC2 destination-address address-set IPSEC2 action permit rule name IPLINK -----------------放行IP-LINK source-zone local destination-zone untrust destination-address 202.100.1.254 mask 255.255.255.255 service icmp action permit 第五步:测试检查
测试检查:
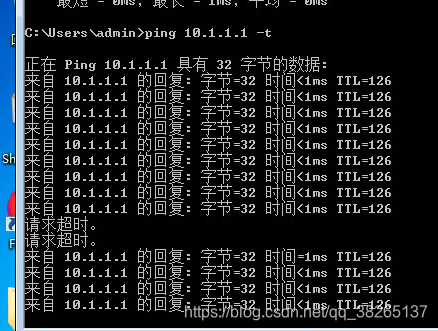
注意:在主备链路备份下当链路发生切换时,会造成丢包。所以建议用隧道模式。
主备链路模式缺点:当主链路DOWN以后切换至备份链路需要重新触发IKE SA IPSEC SA,造成业务中断
IPSec 隧道化链路备份配置 --------华为建议 :
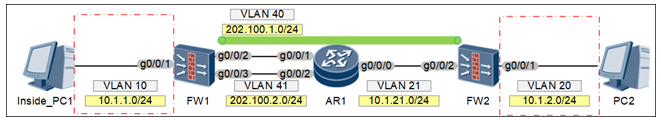
配置思路:
第一步:配置IPSEC VPN
tunnle端口
IPSEC 配置
acl number 3000
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255#
ike proposal 10
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256#
ike peer fw2
pre-shared-key %$%$bJA<~;(;*0TvgC.G_Qs;*0'{%$%$
ike-proposal 10
remote-address 10.1.21.10#
ipsec proposal 10
esp authentication-algorithm sha2-256#
ipsec policy ipsec_policy 10 isakmp
security acl 3000
ike-peer fw2
alias ipsec_policy_10
proposal 10调用在TUNNLE口上interface Tunnel1
ip address 11.1.1.1 255.255.255.0
tunnel-protocol ipsec
ipsec policy ipsec_policy
注意:1. 隧道的地址必须是公网地址,保证可达
AR1需要配置可达路由
ip route-static 11.1.1.1 255.255.255.255 GigabitEthernet0/0/1 202.100.1.10ip route-static 11.1.1.1 255.255.255.255 GigabitEthernet0/0/2 202.100.2.102.tunnle接口必须划进Zone
物理接口端
acl number 3000
rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255#
ike proposal 10
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256#
ike peer fw1
pre-shared-key %$%$6c/0-j#i3UZ#:L0xE:[A_qh_%$%$
ike-proposal 10
remote-address 11.1.1.1 ------------注意,不是指对端的物理接口,所以要可达这个地址
#
ipsec proposal 10
esp authentication-algorithm sha2-256#
ipsec policy ipsec_policy 10 isakmp
security acl 3000
ike-peer fw1
alias ipsec_policy_10
proposal 10interface GigabitEthernet0/0/2
ip address 10.1.21.10 255.255.255.0
ipsec policy ipsec_policy
第二步:配置路由
tunnel端需要引导流量
ip route-static 10.1.2.0 255.255.255.0 Tunnel1
第三步:配置IP-LINK做快速切换
tunnel端
ip-link check enable
ip-link 1 destination 202.100.1.254 interface GigabitEthernet0/0/2 mode icmp
ip-link 2 destination 202.100.2.254 interface GigabitEthernet0/0/3 mode icmp
ip route-static 0.0.0.0 0.0.0.0 202.100.1.254 track ip-link 1
ip route-static 0.0.0.0 0.0.0.0 202.100.2.254 track ip-link 2第四步:放行安全策略
security-policy
rule name IPSEC1
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address address-set IPSEC1
destination-address address-set IPSEC1
service ISAKMP
service esp
action permit
rule name IPSEC2
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address address-set IPSEC2
destination-address address-set IPSEC2
action permit
rule name IP_LINK
source-zone local
destination-zone untrust
destination-address 202.100.1.254 mask 255.255.255.255
destination-address 202.100.2.254 mask 255.255.255.255
service icmp
action permit
第五步:测试检查
dis ike sa
dis ipsec sa注意:隧道地址必须是公网地址,可达的。
总结:隧道备份方式
优点:当物理接口DOWN了,不影响IPSEC隧道的SA,不会影响业务的中断
缺点:隧道接口需要一个公网IP地址。
解决设备单点故障
解决方案概述:
双机单ISP,可能会存在一个运营商链路故障
双机双ISP,最终完美解决方案。
IPSec 双机热备主备备份配置:
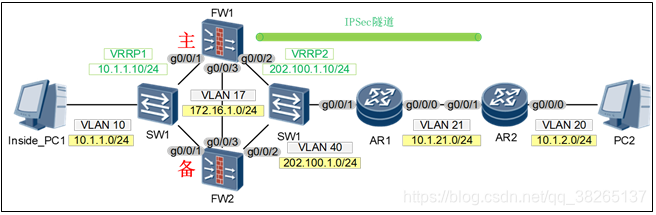
配置思路:
第一步:配置双机热备1.配置VRRP及VGMPinterface GigabitEthernet0/0/1 ip address 10.1.1.10 255.255.255.0 vrrp vrid 1 virtual-ip 10.1.1.254 active # interface GigabitEthernet0/0/2 ip address 202.100.1.10 255.255.255.0 vrrp vrid 2 virtual-ip 202.100.1.253 active 2.配置心跳线 hrp interface GigabitEthernet0/0/3 3.启动HRP及配置主备 主设备配置 hrp enable hrp active-device ---------如果是主,默认可以不敲 备设备配置 hrp enable hrp standby-device 注意:双机热备要成功 第二步:配置IPSEC VPN 如果是主备方式,只需要在主设备配置就可以了,备设备同步IPSEC配置 # acl number 3000 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255# ike proposal 1 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256# ike peer ike17317255503 exchange-mode auto pre-shared-key %$%$T>QPQR$Oi,EyB&E^~`B2Kqh_%$%$ ike-proposal 1 undo version 2 remote-id-type none remote-address 202.100.2.10# ipsec proposal prop17317255503 encapsulation-mode auto esp authentication-algorithm sha2-256 sha1 # ipsec policy ipsec1731725555 1 isakmp security acl 3000 ike-peer ike17317255503 alias IPSEC_VPN proposal prop17317255503 local-address 202.100.1.253 -------------注意点:本地地址不是物理接口地址,是虚拟IP地址 sa duration traffic-based 200000000 sa duration time-based 3600调用IPSECinterface GigabitEthernet0/0/2 ip address 202.100.1.10 255.255.255.0 vrrp vrid 2 virtual-ip 202.100.1.253 active -------只在ACTIVE接口调用 ipsec policy ipsec1731725555 auto-neg 第三步:放行安全策略 security-policy rule name IPSEC1 source-zone local source-zone untrust destination-zone local destination-zone untrust source-address address-set IPSEC1 destination-address address-set IPSEC1 service ISAKMP service esp action permit rule name IPSEC2 source-zone trust source-zone untrust destination-zone trust destination-zone untrust source-address address-set IPSEC2 destination-address address-set IPSEC2 action permit # 第四步: 测试检查 DOWN掉防火墙接口或者DOWN掉主防火墙,可以正常通行
双机单ISP缺点:链路故障
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/8438.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
打赏
 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~

 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~休息一下~~


