说明:
基于路由而不是基于策略的方式(可以跑ospf了)
采用基于iptable mangle修改ip包mark的技术,而不是基于具体leftsubnet和基于rightsubnet的策略,需要了解linux的vti tunnel设备
本文最关键的信息: ipsec.conf的mark 12 就是ip tunnel命令对应的key12.
mark=12
ip tunnel add vti12 mode vti local 12.12.12.1 remote 12.12.12.2 key 12
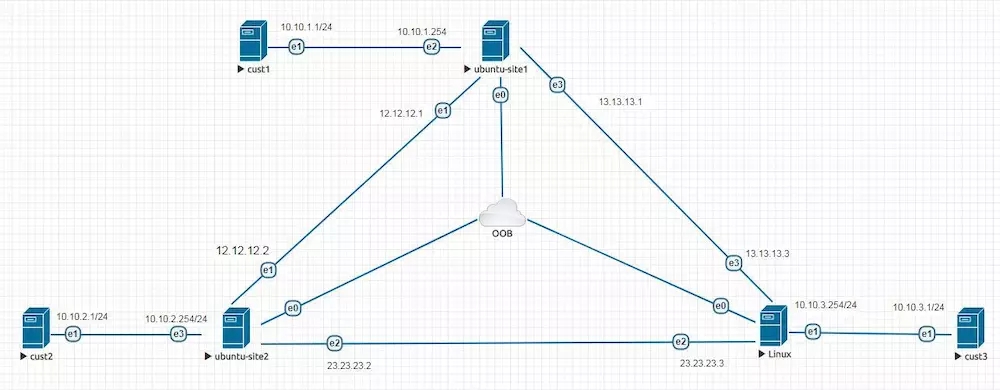
在ubuntu-site,ubuntu-site2,ubuntu-site3上安装strongswan
apt install strongswan -y
root@ubuntu-site1:~# cat test.sh
ip add add 12.12.12.1/24 dev ens4;
ip link set ens4 up;
ip add add 13.13.13.1/24 dev ens6;
ip link set ens6 up;
ip add add 10.10.1.254/24 dev ens5;
ip link set ens5 up;
ip tunnel add vti12 mode vti local 12.12.12.1 remote 12.12.12.2 key 12
ip tunnel add vti13 mode vti local 13.13.13.1 remote 13.13.13.3 key 13
ip add add 112.112.112.1/24 dev vti12
ip add add 113.113.113.1/24 dev vti13
ip link set vti12 up
ip link set vti13 up
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv4.conf.vti12.disable_policy=1
sysctl -w net.ipv4.conf.vti13.disable_policy=1
root@ubuntu-site1:~# cat /etc/ipsec.conf | grep -v "^#"
config setup
conn %default
authby=psk
type=tunnel
conn site1-site2
leftid=12.12.12.1
left=12.12.12.1
leftsubnet=0.0.0.0/0
rightid=12.12.12.2
right=12.12.12.2
rightsubnet=0.0.0.0/0
authby=psk
mark=12
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
conn site1-site3
leftid=13.13.13.1
left=13.13.13.1
leftsubnet=0.0.0.0/0
rightid=13.13.13.3
right=13.13.13.3
rightsubnet=0.0.0.0/0
authby=psk
mark=13
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
root@ubuntu-site1:~# cat /etc/ipsec.secrets | grep -v "^#"
%any %any : PSK "yourPassword123"
修改以下两行为no,并去掉行前面的#
root@ubuntu-site1:~# vi /etc/strongswan.d/charon.conf
install_routes = no
install_virtual_ip = no
root@ubuntu-site2:~# cat test.sh
ip add add 12.12.12.2/24 dev ens4;
ip link set ens4 up;
ip add add 23.23.23.2/24 dev ens5
ip link set ens5 up;
ip add add 10.10.2.254/24 dev ens6;
ip link set ens6 up;
ip tunnel add vti12 mode vti local 12.12.12.2 remote 12.12.12.1 key 12
ip tunnel add vti23 mode vti local 23.23.23.2 remote 23.23.23.3 key 23
ip add add 112.112.112.2/24 dev vti12
ip add add 123.123.123.2/24 dev vti23
ip link set vti12 up
ip link set vti23 up
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv4.conf.vti12.disable_policy=1
sysctl -w net.ipv4.conf.vti23.disable_policy=1
root@ubuntu-site2:~# cat /etc/ipsec.conf | grep -v "^#"
config setup
conn %default
authby=psk
type=tunnel
conn site2-site1
leftid=12.12.12.2
left=12.12.12.2
leftsubnet=0.0.0.0/0
rightid=12.12.12.1
right=12.12.12.1
rightsubnet=0.0.0.0/0
mark=12
authby=psk
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
conn site2-site3
leftid=23.23.23.2
left=23.23.23.2
leftsubnet=0.0.0.0/0
rightid=23.23.23.3
right=23.23.23.3
rightsubnet=0.0.0.0/0
mark=23
authby=psk
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
root@ubuntu-site2:~# cat /etc/ipsec.secrets | grep -v "^#"
%any %any : PSK "yourPassword123"
修改以下两行为no,并去掉行前面的#
root@ubuntu-site2:~# vi /etc/strongswan.d/charon.conf
install_routes = no
install_virtual_ip = no
root@ubuntu-site3:~# cat test.sh
ip add add 13.13.13.3/24 dev ens6;
ip link set ens6 up;
ip add add 23.23.23.3/24 dev ens5
ip link set ens5 up;
ip add add 10.10.3.254/24 dev ens4;
ip link set ens4 up;
ip tunnel add vti13 mode vti local 13.13.13.3 remote 13.13.13.1 key 13
ip tunnel add vti23 mode vti local 23.23.23.3 remote 23.23.23.2 key 23
ip add add 113.113.113.3/24 dev vti13
ip add add 123.123.123.3/24 dev vti23
ip link set vti13 up
ip link set vti23 up
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv4.conf.vti13.disable_policy=1
sysctl -w net.ipv4.conf.vti23.disable_policy=1
root@ubuntu-site3:~# cat /etc/ipsec.conf | grep -v "^#"
config setup
conn %default
authby=psk
type=tunnel
conn site3-site1
leftid=13.13.13.3
left=13.13.13.3
leftsubnet=0.0.0.0/0
rightid=13.13.13.1
right=13.13.13.1
rightsubnet=0.0.0.0/0
mark=13
authby=psk
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
conn site3-site2
leftid=23.23.23.3
left=23.23.23.3
leftsubnet=0.0.0.0/0
rightid=23.23.23.2
right=23.23.23.2
rightsubnet=0.0.0.0/0
mark=23
authby=psk
auto=route
keyexchange=ikev1
ike=aes-sha1-modp1024
ikelifetime=86400s
esp=aes-sha1-modp1024
lifetime=86400s
type=tunnel
root@ubuntu-site3:~# cat /etc/ipsec.secrets | grep -v "^#"
%any %any : PSK "yourPassword123"
修改以下两行为no,并去掉行前面的#
root@ubuntu-site3:~# vi /etc/strongswan.d/charon.conf
install_routes = no
install_virtual_ip = no
在ubuntu-site1,ubuntu-site2,ubuntu-site3上配置quagga的ospfd
root@ubuntu-site1:~# cat /etc/quagga/ospfd.conf
! Zebra configuration saved from vty
! 2017/12/19 03:54:16
hostname ubuntu-site1
password zebra
log stdout
interface ens3
interface ens4
interface ens5
interface ens6
!
interface ens7
interface ens8
interface ip_vti0
interface lo
ip ospf network point-to-point
interface vti12
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 12 md5 test123
interface vti13
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 13 md5 test123
router ospf
ospf router-id 1.1.1.1
network 10.10.1.0/24 area 0.0.0.0
network 112.112.112.0/24 area 0.0.0.0
network 113.113.113.0/24 area 0.0.0.0
area 0.0.0.0 authentication message-digest
line vty
root@ubuntu-site2:~# cat /etc/quagga/ospfd.conf
hostname ubuntu-site2
password zebra
log stdout
interface ens3
interface ens4
interface ens5
interface ens6
interface ens7
interface ens8
interface ip_vti0
interface lo
ip ospf network point-to-point
interface vti12
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 12 md5 test123
interface vti23
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 23 md5 test123
router ospf
ospf router-id 2.2.2.2
network 10.10.2.0/24 area 0.0.0.0
network 112.112.112.0/24 area 0.0.0.0
network 123.123.123.0/24 area 0.0.0.0
area 0.0.0.0 authentication message-digest
line vty
root@ubuntu-site3:~# cat /etc/quagga/ospfd.conf
hostname ubuntu-site3
password zebra
log stdout
interface ens3
interface ens4
interface ens5
interface ens6
interface ens7
interface ens8
interface ip_vti0
interface lo
ip ospf network point-to-point
interface vti13
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 13 md5 test123
interface vti23
ip ospf network broadcast
ip ospf authentication message-digest
ip ospf message-digest-key 23 md5 test123
router ospf
ospf router-id 3.3.3.3
network 10.10.3.0/24 area 0.0.0.0
network 113.113.113.0/24 area 0.0.0.0
network 123.123.123.0/24 area 0.0.0.0
area 0.0.0.0 authentication message-digest
line vty
启动
sh test.sh
systemctl enable strongswan
systemctl start strongswan
systemctl enable zebra
systemctl start zebra
systemctl enable ospfd
systemctl start ospfd


root@ubuntu-site1:~# ip xfrm policy
src 0.0.0.0/0 dst 0.0.0.0/0
dir fwd priority 200000
mark 0xd/0xffffffff
tmpl src 13.13.13.3 dst 13.13.13.1
proto esp reqid 2 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
dir in priority 200000
mark 0xd/0xffffffff
tmpl src 13.13.13.3 dst 13.13.13.1
proto esp reqid 2 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
dir out priority 200000
mark 0xd/0xffffffff
tmpl src 13.13.13.1 dst 13.13.13.3
proto esp reqid 2 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
dir fwd priority 200000
mark 0xc/0xffffffff
tmpl src 12.12.12.2 dst 12.12.12.1
proto esp reqid 1 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
dir in priority 200000
mark 0xc/0xffffffff
tmpl src 12.12.12.2 dst 12.12.12.1
proto esp reqid 1 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
dir out priority 200000
mark 0xc/0xffffffff
tmpl src 12.12.12.1 dst 12.12.12.2
proto esp reqid 1 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
socket in priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket out priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket in priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket out priority 0
src ::/0 dst ::/0
socket in priority 0
src ::/0 dst ::/0
socket out priority 0
src ::/0 dst ::/0
socket in priority 0
src ::/0 dst ::/0
socket out priority 0
注意mark匹配ip tunnel vtiXX中的key(mark 0xd/0xffffffff对应key 13,mark 0xc/0xffffffff对应key12)
root@ubuntu-site1:~# ip xfrm state
src 13.13.13.1 dst 13.13.13.3
proto esp spi 0xcb936f43 reqid 2 mode tunnel
replay-window 0 flag af-unspec
mark 0xd/0xffffffff
auth-trunc hmac(sha1) 0x99f7cf5847e85d52699a76a6b6863dce2233e2a2 96
enc cbc(aes) 0x08951b4da582a4b8096cffd283b6c0db
anti-replay context: seq 0x0, oseq 0x1ab, bitmap 0x00000000
src 13.13.13.3 dst 13.13.13.1
proto esp spi 0xc8ee8e70 reqid 2 mode tunnel
replay-window 32 flag af-unspec
mark 0xd/0xffffffff
auth-trunc hmac(sha1) 0x622d957d23a6b69fadeca0ef10bdd8696ec54cc5 96
enc cbc(aes) 0xc99a48dcb79ca04a62c655abfe0f704d
anti-replay context: seq 0x1a4, oseq 0x0, bitmap 0xffffffff
src 13.13.13.1 dst 13.13.13.3
proto esp spi 0xc4bb8475 reqid 2 mode tunnel
replay-window 0 flag af-unspec
mark 0xd/0xffffffff
auth-trunc hmac(sha1) 0x23e40fbacd044a2d21969f0a3dc204128b187495 96
enc cbc(aes) 0x1ff38fc5c997a65491fde7ede0184627
anti-replay context: seq 0x0, oseq 0x1, bitmap 0x00000000
src 13.13.13.3 dst 13.13.13.1
proto esp spi 0xce3373c0 reqid 2 mode tunnel
replay-window 32 flag af-unspec
mark 0xd/0xffffffff
auth-trunc hmac(sha1) 0x76ed53e160ef908aa3d381a2337f2c1921802cf3 96
enc cbc(aes) 0x15538642e1983157e9ac3a1956b67b2e
anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001
src 12.12.12.1 dst 12.12.12.2
proto esp spi 0xc7be0ad2 reqid 1 mode tunnel
replay-window 0 flag af-unspec
mark 0xc/0xffffffff
auth-trunc hmac(sha1) 0x26b941a9ca7ab156b545486fe4ba9967625049f3 96
enc cbc(aes) 0xe586940a0e6265f48b135f17a222bae8
anti-replay context: seq 0x0, oseq 0x1, bitmap 0x00000000
src 12.12.12.2 dst 12.12.12.1
proto esp spi 0xcda369d5 reqid 1 mode tunnel
replay-window 32 flag af-unspec
mark 0xc/0xffffffff
auth-trunc hmac(sha1) 0x96501613cbb699118e63584db9880d7b4cc7d135 96
enc cbc(aes) 0x2f68b9b2eae0c4fba759eb1afd1bc261
anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001
src 12.12.12.1 dst 12.12.12.2
proto esp spi 0xcee6d254 reqid 1 mode tunnel
replay-window 0 flag af-unspec
mark 0xc/0xffffffff
auth-trunc hmac(sha1) 0x18bb43e1a59f53713e133d684c8df4bbde7accd9 96
enc cbc(aes) 0x43ccaacd92ed25b3fa69446407824ece
anti-replay context: seq 0x0, oseq 0x1a8, bitmap 0x00000000
src 12.12.12.2 dst 12.12.12.1
proto esp spi 0xc3a6a595 reqid 1 mode tunnel
replay-window 32 flag af-unspec
mark 0xc/0xffffffff
auth-trunc hmac(sha1) 0x0472d720f642f64ba73ef727715b8dcf13104cda 96
enc cbc(aes) 0xee949f41182e5610987e52e3dcb5ac04
anti-replay context: seq 0x19a, oseq 0x0, bitmap 0xffffffff
查看SPD(安全策略数据库)
root@ubuntu-site1:~# setkey -DP
0.0.0.0/0[any] 0.0.0.0/0[any] 255
fwd prio high + 1073541824 ipsec
esp/tunnel/13.13.13.3-13.13.13.1/unique:2
created: Dec 19 07:00:34 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=106 seq=1 pid=1971
refcnt=1
0.0.0.0/0[any] 0.0.0.0/0[any] 255
in prio high + 1073541824 ipsec
esp/tunnel/13.13.13.3-13.13.13.1/unique:2
created: Dec 19 07:00:34 2017 lastused: Dec 19 07:02:48 2017
lifetime: 0(s) validtime: 0(s)
spid=96 seq=2 pid=1971
refcnt=5
0.0.0.0/0[any] 0.0.0.0/0[any] 255
out prio high + 1073541824 ipsec
esp/tunnel/13.13.13.1-13.13.13.3/unique:2
created: Dec 19 07:00:34 2017 lastused: Dec 19 07:02:48 2017
lifetime: 0(s) validtime: 0(s)
spid=89 seq=3 pid=1971
refcnt=6
0.0.0.0/0[any] 0.0.0.0/0[any] 255
fwd prio high + 1073541824 ipsec
esp/tunnel/12.12.12.2-12.12.12.1/unique:1
created: Dec 19 07:00:30 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=82 seq=4 pid=1971
refcnt=1
0.0.0.0/0[any] 0.0.0.0/0[any] 255
in prio high + 1073541824 ipsec
esp/tunnel/12.12.12.2-12.12.12.1/unique:1
created: Dec 19 07:00:30 2017 lastused: Dec 19 07:02:48 2017
lifetime: 0(s) validtime: 0(s)
spid=72 seq=5 pid=1971
refcnt=5
0.0.0.0/0[any] 0.0.0.0/0[any] 255
out prio high + 1073541824 ipsec
esp/tunnel/12.12.12.1-12.12.12.2/unique:1
created: Dec 19 07:00:30 2017 lastused: Dec 19 07:02:48 2017
lifetime: 0(s) validtime: 0(s)
spid=65 seq=6 pid=1971
refcnt=5
(per-socket policy)
in(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=59 seq=7 pid=1971
refcnt=1
(per-socket policy)
out(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=52 seq=8 pid=1971
refcnt=1
(per-socket policy)
in(socket) none
created: Dec 19 06:49:13 2017 lastused: Dec 19 07:00:44 2017
lifetime: 0(s) validtime: 0(s)
spid=43 seq=9 pid=1971
refcnt=1
(per-socket policy)
out(socket) none
created: Dec 19 06:49:13 2017 lastused: Dec 19 07:00:34 2017
lifetime: 0(s) validtime: 0(s)
spid=36 seq=10 pid=1971
refcnt=1
(per-socket policy)
in(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=27 seq=11 pid=1971
refcnt=1
(per-socket policy)
out(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=20 seq=12 pid=1971
refcnt=1
(per-socket policy)
in(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=11 seq=13 pid=1971
refcnt=1
(per-socket policy)
out(socket) none
created: Dec 19 06:49:13 2017 lastused:
lifetime: 0(s) validtime: 0(s)
spid=4 seq=0 pid=1971
refcnt=1
查看SAD(安全关联数据库)
root@ubuntu-site1:~# setkey -D
13.13.13.1 13.13.13.3
esp mode=tunnel spi=3360855121(0xc8529451) reqid=2(0x00000002)
E: aes-cbc a26369f6 8bdb2e43 a1bb2918 e36ba8f3
A: hmac-sha1 e523f171 72accb59 b9f51a5b c698095e 5184cedb
seq=0x00000000 replay=0 flags=0x00000000 state=mature
created: Dec 19 07:00:34 2017 current: Dec 19 07:02:50 2017
diff: 136(s) hard: 86400(s) soft: 85677(s)
last: Dec 19 07:00:43 2017 hard: 0(s) soft: 0(s)
current: 4464(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 48 hard: 0 soft: 0
sadb_seq=1 pid=1972 refcnt=0
13.13.13.3 13.13.13.1
esp mode=tunnel spi=3480093042(0xcf6e0172) reqid=2(0x00000002)
E: aes-cbc 099ce266 f60dc968 a4cb5a16 88bf4cd0
A: hmac-sha1 2b181746 d3779042 9d4d1a55 f14ae3df c58e06eb
seq=0x00000000 replay=32 flags=0x00000000 state=mature
created: Dec 19 07:00:34 2017 current: Dec 19 07:02:50 2017
diff: 136(s) hard: 86400(s) soft: 85665(s)
last: Dec 19 07:00:34 2017 hard: 0(s) soft: 0(s)
current: 3968(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 43 hard: 0 soft: 0
sadb_seq=2 pid=1972 refcnt=0
13.13.13.1 13.13.13.3
esp mode=tunnel spi=3393478515(0xca445f73) reqid=2(0x00000002)
E: aes-cbc 5351941a c364249f 1e0c6eb2 d1613e82
A: hmac-sha1 e8187858 83e01872 9ecacdb0 d476d10b 6555b5ed
seq=0x00000000 replay=0 flags=0x00000000 state=mature
created: Dec 19 07:00:34 2017 current: Dec 19 07:02:50 2017
diff: 136(s) hard: 86400(s) soft: 85718(s)
last: hard: 0(s) soft: 0(s)
current: 0(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 0 hard: 0 soft: 0
sadb_seq=3 pid=1972 refcnt=0
13.13.13.3 13.13.13.1
esp mode=tunnel spi=3296380225(0xc47ac541) reqid=2(0x00000002)
E: aes-cbc 40f291cf 772178a3 bb26fe53 d027cd16
A: hmac-sha1 58804de6 0edc3237 5cd9ea8a 3714a46d 163bf838
seq=0x00000000 replay=32 flags=0x00000000 state=mature
created: Dec 19 07:00:34 2017 current: Dec 19 07:02:50 2017
diff: 136(s) hard: 86400(s) soft: 85406(s)
last: hard: 0(s) soft: 0(s)
current: 0(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 0 hard: 0 soft: 0
sadb_seq=4 pid=1972 refcnt=0
12.12.12.1 12.12.12.2
esp mode=tunnel spi=3250042971(0xc1b7b85b) reqid=1(0x00000001)
E: aes-cbc 45b6da2a 7505c680 56ab1dcd 29ae3e44
A: hmac-sha1 0c3cb351 914d9ddb b11a1cdf c31ba7ee a60d016b
seq=0x00000000 replay=0 flags=0x00000000 state=mature
created: Dec 19 07:00:30 2017 current: Dec 19 07:02:50 2017
diff: 140(s) hard: 86400(s) soft: 85651(s)
last: Dec 19 07:00:33 2017 hard: 0(s) soft: 0(s)
current: 80(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 1 hard: 0 soft: 0
sadb_seq=5 pid=1972 refcnt=0
12.12.12.2 12.12.12.1
esp mode=tunnel spi=3341131662(0xc7259f8e) reqid=1(0x00000001)
E: aes-cbc 90a10620 7f5b61bd 63db530f 7d7f9a43
A: hmac-sha1 4d5d5b05 4456b648 cacbf1f0 28fe95c3 21cfdeec
seq=0x00000000 replay=32 flags=0x00000000 state=mature
created: Dec 19 07:00:30 2017 current: Dec 19 07:02:50 2017
diff: 140(s) hard: 86400(s) soft: 85329(s)
last: Dec 19 07:00:30 2017 hard: 0(s) soft: 0(s)
current: 40(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 1 hard: 0 soft: 0
sadb_seq=6 pid=1972 refcnt=0
12.12.12.1 12.12.12.2
esp mode=tunnel spi=3325113718(0xc6313576) reqid=1(0x00000001)
E: aes-cbc 0dc38937 81698fb7 8130137b 9e422713
A: hmac-sha1 982a5d1a 3063976d 3158712f a6f33f64 1e16de72
seq=0x00000000 replay=0 flags=0x00000000 state=mature
created: Dec 19 07:00:30 2017 current: Dec 19 07:02:50 2017
diff: 140(s) hard: 86400(s) soft: 85678(s)
last: Dec 19 07:00:43 2017 hard: 0(s) soft: 0(s)
current: 3440(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 38 hard: 0 soft: 0
sadb_seq=7 pid=1972 refcnt=0
12.12.12.2 12.12.12.1
esp mode=tunnel spi=3334662797(0xc6c2ea8d) reqid=1(0x00000001)
E: aes-cbc ab4e8a7b 35b32aa6 da98441f ba5d8be1
A: hmac-sha1 b4acba9e 0fd0818e 0a7c3e5a 1cbd572a de41811d
seq=0x00000000 replay=32 flags=0x00000000 state=mature
created: Dec 19 07:00:30 2017 current: Dec 19 07:02:50 2017
diff: 140(s) hard: 86400(s) soft: 85469(s)
last: Dec 19 07:00:40 2017 hard: 0(s) soft: 0(s)
current: 3216(bytes) hard: 0(bytes) soft: 0(bytes)
allocated: 36 hard: 0 soft: 0
sadb_seq=0 pid=1972 refcnt=0
REF:
https://wiki.strongswan.org/projects/strongswan/wiki/RouteBasedVPN
https://wiki.strongswan.org/projects/strongswan/wiki/ForwardingAndSplitTunneling
vpn" target="_blank" rel="nofollow">https://vincent.bernat.im/en/blog/2017-route-based-vpn
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/365.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~