



1、AR路由器配置IKE方式的IPSec VPNIPSec(Internet Protocol Security)是IETF(Internet Engineering Task Force)制定的一组开放的网络安全协议,在IP层通过数据来源认证、数据加密、数据完整性和抗重放功能来保证通信双方Internet上传输数据的安全性。在Internet的传输中,绝大部分数据的内容都是明文传输的,这样就会存在很多潜在的危险,比如:密码、银行帐户的信息被窃取、篡改,用户的身份被冒充,遭受网络恶意攻击等。网络中部署IPSec后,可对传输的数据进行保护处理,降低信息泄漏的风险。采用默认配置通过IKE协商方式建立I
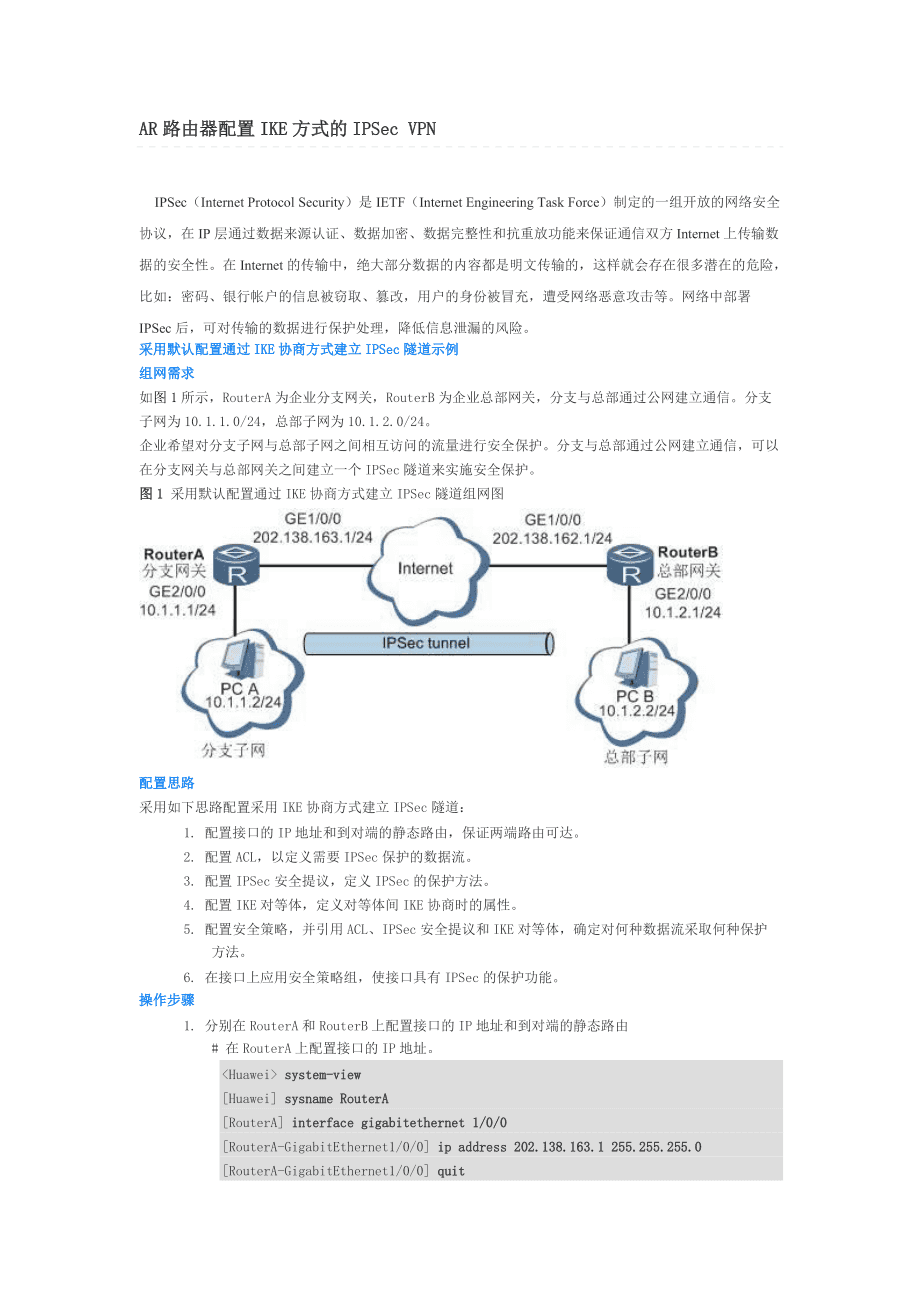
2、PSec隧道示例组网需求如图1所示,RouterA为企业分支网关,RouterB为企业总部网关,分支与总部通过公网建立通信。分支子网为10.1.1.0/24,总部子网为10.1.2.0/24。企业希望对分支子网与总部子网之间相互访问的流量进行安全保护。分支与总部通过公网建立通信,可以在分支网关与总部网关之间建立一个IPSec隧道来实施安全保护。图1采用默认配置通过IKE协商方式建立IPSec隧道组网图配置思路采用如下思路配置采用IKE协商方式建立IPSec隧道:1.配置接口的IP地址和到对端的静态路由,保证两端路由可达。2.配置ACL,以定义需要IPSec保护的数据流。3.配置IPSec安全提
3、议,定义IPSec的保护方法。4.配置IKE对等体,定义对等体间IKE协商时的属性。5.配置安全策略,并引用ACL、IPSec安全提议和IKE对等体,确定对何种数据流采取何种保护方法。6.在接口上应用安全策略组,使接口具有IPSec的保护功能。操作步骤1.分别在RouterA和RouterB上配置接口的IP地址和到对端的静态路由#在RouterA上配置接口的IP地址。system-viewHuaweisysname RouterARouterAinterface gigabitethernet 1/0/0RouterA-GigabitEthernet1/0/0ip address 202.13
4、8.163.1 255.255.255.0RouterA-GigabitEthernet1/0/0quitRouterAinterface gigabitethernet 2/0/0RouterA-GigabitEthernet2/0/0ip address 10.1.1.1 255.255.255.0RouterA-GigabitEthernet2/0/0quit#在RouterA上配置到对端的静态路由,此处假设到对端的下一跳地址为202.138.163.2。RouterAip route-static 202.138.162.0 255.255.255.0 202.138.163.2Rou
5、terAip route-static 10.1.2.0 255.255.255.0 202.138.163.2#在RouterB上配置接口的IP地址。system-viewHuaweisysname RouterBRouterBinterface gigabitethernet 1/0/0RouterB-GigabitEthernet1/0/0ip address 202.138.162.1 255.255.255.0RouterB-GigabitEthernet1/0/0quitRouterBinterface gigabitethernet 2/0/0RouterB-GigabitEth
6、ernet2/0/0ip address 10.1.2.1 255.255.255.0RouterB-GigabitEthernet2/0/0quit#在RouterB上配置到对端的静态路由,此处假设到对端下一跳地址为202.138.162.2。RouterBip route-static 202.138.163.0 255.255.255.0 202.138.162.2RouterBip route-static 10.1.1.0 255.255.255.0 202.138.162.22.分别在RouterA和RouterB上配置ACL,定义各自要保护的数据流#在RouterA上配置ACL,
7、定义由子网10.1.1.0/24去子网10.1.2.0/24的数据流。RouterAacl number 3101RouterA-acl-adv-3101rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255RouterA-acl-adv-3101quit#在RouterB上配置ACL,定义由子网10.1.2.0/24去子网10.1.1.0/24的数据流。RouterBacl number 3101RouterB-acl-adv-3101rule permit ip source 10.1.2.0 0.0.
8、0.255 destination 10.1.1.0 0.0.0.255RouterB-acl-adv-3101quit3.分别在RouterA和RouterB上创建IPSec安全提议#在RouterA上配置IPSec安全提议。RouterAipsec proposal tran1RouterA-ipsec-proposal-tran1quit#在RouterB上配置IPSec安全提议。RouterBipsec proposal tran1RouterB-ipsec-proposal-tran1quit此时分别在RouterA和RouterB上执行display ipsec proposal会
9、显示所配置的信息。4.分别在RouterA和RouterB上配置IKE对等体说明:该示例中没有配置IKE安全提议,采用的是系统提供的一条缺省的IKE安全提议。#在RouterA上配置IKE对等体,并根据默认配置,配置预共享密钥和对端ID。RouterAike peer spub v1RouterA-ike-peer-spubpre-shared-key simple huaweiRouterA-ike-peer-spubremote-address 202.138.162.1RouterA-ike-peer-spubquit#在RouterB上配置IKE对等体,并根据默认配置,配置预共享密钥和
10、对端ID。RouterBike peer spua v1RouterB-ike-peer-spuapre-shared-key simple huaweiRouterB-ike-peer-spuaremote-address 202.138.163.1RouterB-ike-peer-spuaquit此时分别在RouterA和RouterB上执行display ike peer会显示所配置的信息,以RouterA为例。RouterAdisplay ike peer name spub verbose-Peer name: spubExchange mode: main on phase 1Pr
11、e-shared-key: huaweiLocal ID type: IPDPD: DisableDPD mode: PeriodicDPD idle time: 30DPD retransmit interval: 15DPD retry limit: 3Host name:Peer Ip address: 202.138.162.1VPN name:Local IP address:Remote name:Nat-traversal: DisableConfigured IKE version: Version onePKI realm: NULLInband OCSP: DisableL
12、ifetime notification: Enable-5.分别在RouterA和RouterB上创建安全策略#在RouterA上配置IKE动态协商方式安全策略。RouterAipsec policy map1 10 isakmpRouterA-ipsec-policy-isakmp-map1-10ike-peer spubRouterA-ipsec-policy-isakmp-map1-10proposal tran1RouterA-ipsec-policy-isakmp-map1-10security acl 3101RouterA-ipsec-policy-isakmp-map1-10
13、quit#在RouterB上配置IKE动态协商方式安全策略。RouterBipsec policy use1 10 isakmpRouterB-ipsec-policy-isakmp-use1-10ike-peer spuaRouterB-ipsec-policy-isakmp-use1-10proposal tran1RouterB-ipsec-policy-isakmp-use1-10security acl 3101RouterB-ipsec-policy-isakmp-use1-10quit此时分别在RouterA和RouterB上执行display ipsec policy会显示所配
14、置的信息。6.分别在RouterA和RouterB的接口上应用各自的安全策略组,使接口具有IPSec的保护功能#在RouterA的接口上引用安全策略组。RouterAinterface gigabitethernet 1/0/0RouterA-GigabitEthernet1/0/0ipsec policy map1RouterA-GigabitEthernet1/0/0quit#在RouterB的接口上引用安全策略组。RouterBinterface gigabitethernet 1/0/0RouterB-GigabitEthernet1/0/0ipsec policy use1Route
15、rB-GigabitEthernet1/0/0quit7.检查配置结果#配置成功后,在主机PC A执行ping操作仍然可以ping通主机PC B,它们之间的数据传输将被加密,执行命令display ipsec statistics esp可以查看数据包的统计信息。#在RouterA上执行display ike sa操作,结果如下。RouterAdisplay ike saConn-IDPeerVPNFlag(s)Phase-16202.138.162.10RD|ST214202.138.162.10RD|ST1Flag Description:RD-READYST-STAYALIVERL-RE
16、PLACEDFD-FADINGTO-TIMEOUTHRT-HEARTBEATLKG-LAST KNOWN GOOD SEQ NO.BCK-BACKED UP#分别在RouterA和RouterB上执行display ipsec sa会显示所配置的信息,以RouterA为例。RouterAdisplay ipsec sa=Interface: GigabitEthernet 1/0/0Path MTU: 1500=-IPSec policy name: map1Sequence number: 10Acl Group: 3101Acl rule: 5Mode: ISAKMP-Connection
17、 ID: 16Encapsulation mode: TunnelTunnel local: 202.138.163.1Tunnel remote: 202.138.162.1Flow source: 10.1.1.0/0.0.0.255 0/0Flow destination: 10.1.2.0/0.0.0.255 0/0Qos pre-classify: DisableQos group: -Outbound ESP SAsSPI: 1026037179 (0x3d2815bb)Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5SA remaining ke
18、y duration (bytes/sec): 1887436800/3596Max sent sequence-number: 5UDP encapsulation used for NAT traversal: NInbound ESP SAsSPI: 1593054859 (0x5ef4168b)Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5SA remaining key duration (bytes/sec): 1887436800/3596Max received sequence-number: 4Anti-replay window siz
19、e: 32UDP encapsulation used for NAT traversal: N配置文件RouterA的配置文件#sysname RouterA#acl number 3101rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255#ipsec proposal tran1#ike peer spub v1pre-shared-key simple huaweiremote-address 202.138.162.1#ipsec policy map1 10 isakmpsecurity acl 3101ike-peer spubproposal tran1#interface GigabitEthernet1/0/0ip address 202.138.163.1 255.255.255.0ipsec policy map1#interface GigabitEthernet2/0/0ip address 10.1.1.1 255.255.255.0#ip route-static 202.138.162.0 255.255.255.0 202.138.163.2ip route-static 10.1
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4628.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~