
思路:防火墙FW1和FW2设置静态路由丢给AR1,公网部分就可以互通了。
剩下设置vlan和IPSEC
设置静态路由 FW1:ip route-static 0.0.0.0 0.0.0.0 1.1.1.1FW2:ip route-static 0.0.0.0 0.0.0.0 1.1.2.1
设置vlan FW1: interface GigabitEthernet1/0/1.10 vlan-type dot1q 10 ip address 192.168.10.254 255.255.255.0 service-manage ping permit#interface GigabitEthernet1/0/1.20 vlan-type dot1q 20 ip address 192.168.20.254 255.255.255.0 service-manage ping permit LSW1: interface Ethernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 20#interface Ethernet0/0/2 port link-type access port default vlan 10#interface Ethernet0/0/3 port link-type access port default vlan 20
设置IPSEC主要有四个设置:IKE PROPOSAL 、IKE-PEER 、IPSEC PROPOSAL、 ACL感兴趣流 1-ike proposal +数字(1-31位),主要设置ike的封装算法与对端交互
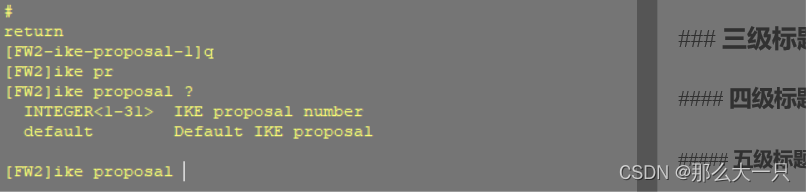
ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256
这里没有要求的话就默认,后面ipsec proposal 一样默认就行
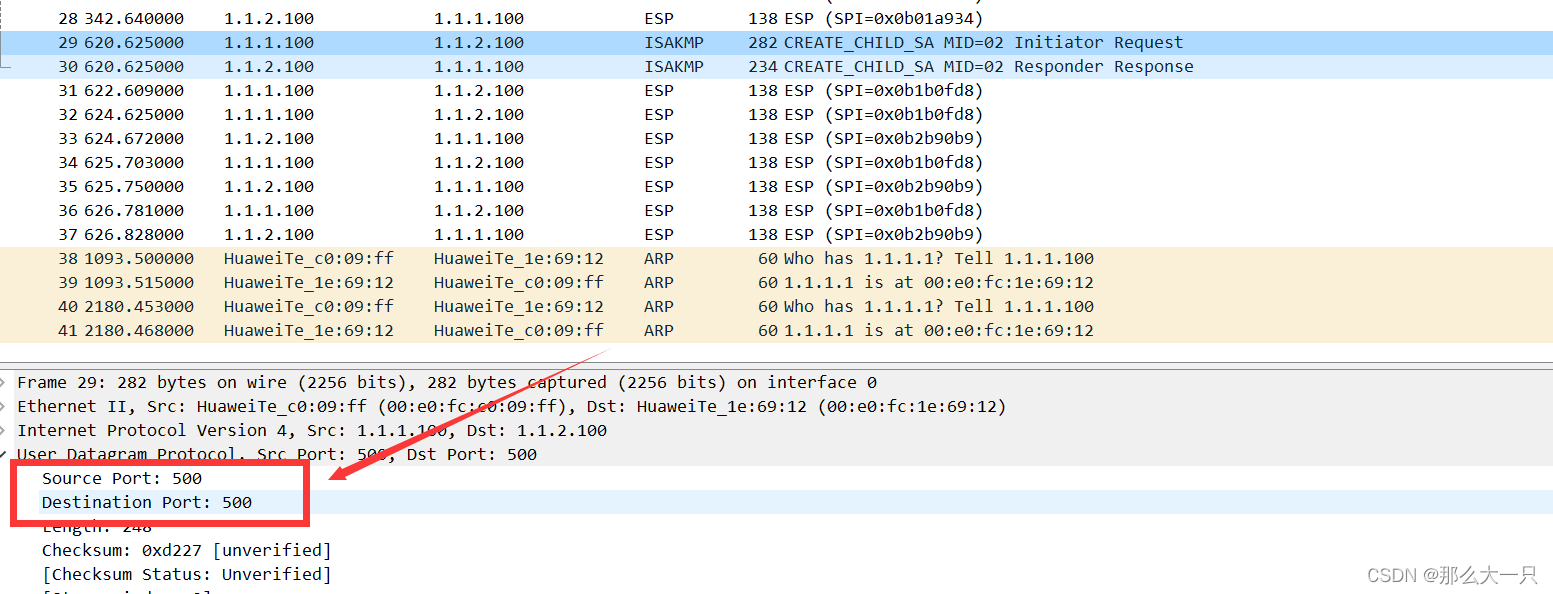
2-设置ike peer,主要设置协商用的密码,应用ike-proposal 和设置对端IP[FW2]ike peer ike[FW2-ike-peer-ike]dis th2022-09-05 11:07:06.070 #ike peer ike pre-shared-key 12345678 ike-proposal 1 remote-address 1.1.1.1003-设置ipsec proposal[FW2-ike-peer-ike]q[FW2]ipsec [FW2]ipsec pr [FW2]ipsec proposal ipsec[FW2-ipsec-proposal-ipsec]dis th2022-09-05 11:11:01.370 #ipsec proposal ipsec esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256#4-设置ACL感兴趣流 FW2: acl number 3000 rule 5 permit ip source 10.126.10.0 0.0.0.255 destination 192.168.10.0 0.0.0.255 rule 10 permit ip source 10.126.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255FW1: acl number 3000 rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 10.126.10.0 0.0.0.255 rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 10.126.10.0 0.0.0.2555-设置ipsec policy[FW2]ipsec po [FW2]ipsec policy FW1 1 is [FW2]ipsec policy FW1 1 isakmp Info: The ISAKMP policy sequence number should be smaller than the template poli cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta ke effect.[FW2-ipsec-policy-isakmp-FW1-1]dis th2022-09-05 11:13:14.450 # 命令解释:ipsec policy +策略名+标识+手动/自动 ipsec policy FW1 1 isakmp security acl 3000 ike-peer ike proposal ipsec6-将ipsec polic 应用到接口上, FW2: interface GigabitEthernet1/0/0 undo shutdown ip address 1.1.1.100 255.255.255.0 service-manage ping permit ipsec policy FW1 对端同样这是即可 剩下的就是安全策略的匹配 ip service-set isakmp type object 16 service 0 protocol udp source-port 500 destination-port 500 这里是将isakmp协议新建了,这里抓包可以看到源目端口号都是500需要放通
名字basic开头是控制基础零流量进出,ipsec开头是控制ipsec的安全联盟流量建立。 FW1: security-policy rule name basic source-zone trust source-address 192.168.10.0 24 source-address 192.168.20.0 24 destination-address 10.126.10.0 24 destination-zone untrust action permit rule name basic_in source-zone untrust source-address 10.126.10.0 24 destination-address 192.168.10.0 24 destination-address 192.168.20.0 24 destination-zone trust action permit rule name ipsec_out source-zone local destination-zone untrust source-address 1.1.1.0 mask 255.255.255.0 destination-address 1.1.2.0 mask 255.255.255.0 service esp service icmp service isakmp action permit rule name ipsec_in source-zone untrust destination-zone local source-address 1.1.2.0 mask 255.255.255.0 destination-address 1.1.1.0 mask 255.255.255.0 service esp service isakmp action permit FW2: security-policy rule name basic source-address 10.126.10.0 24destination-address 192.168.10.0 24destination-address 192.168.20.0 24 source-zone trust destination-zone untrust action permit rule name basic_in source-zone untrust source-address 10.126.10.0 24destination-address 192.168.10.0 24destination-address 192.168.20.0 24 destination-zone trust action permit rule name ipsec_in source-zone untrust destination-zone local source-address 1.1.1.0 mask 255.255.255.0 destination-address 1.1.2.0 mask 255.255.255.0 service esp service protocol udp source-port 500 destination-port 500 action permit rule name ipsec_out source-zone local destination-zone untrust source-address 1.1.2.0 mask 255.255.255.0 destination-address 1.1.1.0 mask 255.255.255.0 service esp service icmp service protocol udp source-port 500 destination-port 500 action permit
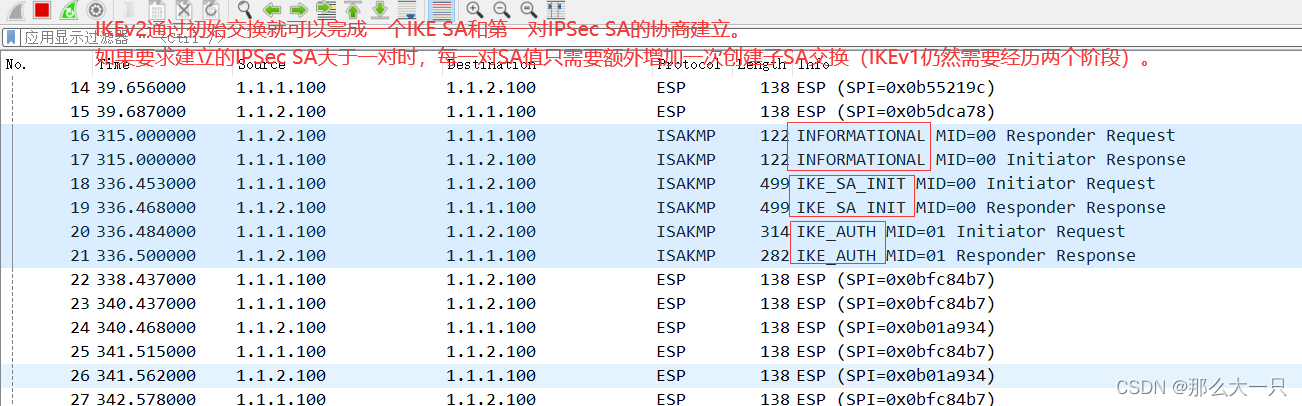
IKEv2初始交换对应IKEv1的第一阶段,初始交换包含两次交换四条消息,如图所示。 消息属于第一次交换(称为IKE_SA_INIT交换),以明文方式完成IKE SA的参数协商,包括协商加密和验证算法,交换临时随机数和DH交换。IKE_SA_INIT交换后生成一个共享密钥材料,通过这个共享密钥材料可以衍生出IPSec SA的所有密钥。 消息③和④属于第二次交换(称为IKE_AUTH交换),以加密方式完成身份认证、对前两条信息的认证和IPSec SA的参数协商。 创建子SA交换包含两条消息,用于一个IKE SA创建多个IPSec SA或IKE的重协商,对应IKEv1的第二阶段。该交换必须在初始交换完成后进行,交换消息由初始交换协商的密钥进行保护。如果启用PFS,创建子SA交换需要额外进行一次DH交换,生成新的密钥材料。 生成密钥材料后,子SA的所有密钥都从这个密钥材料衍生出来。该交换的发起者可以是初始交换的协商发起方,也可以是初始交换的协商响应方。

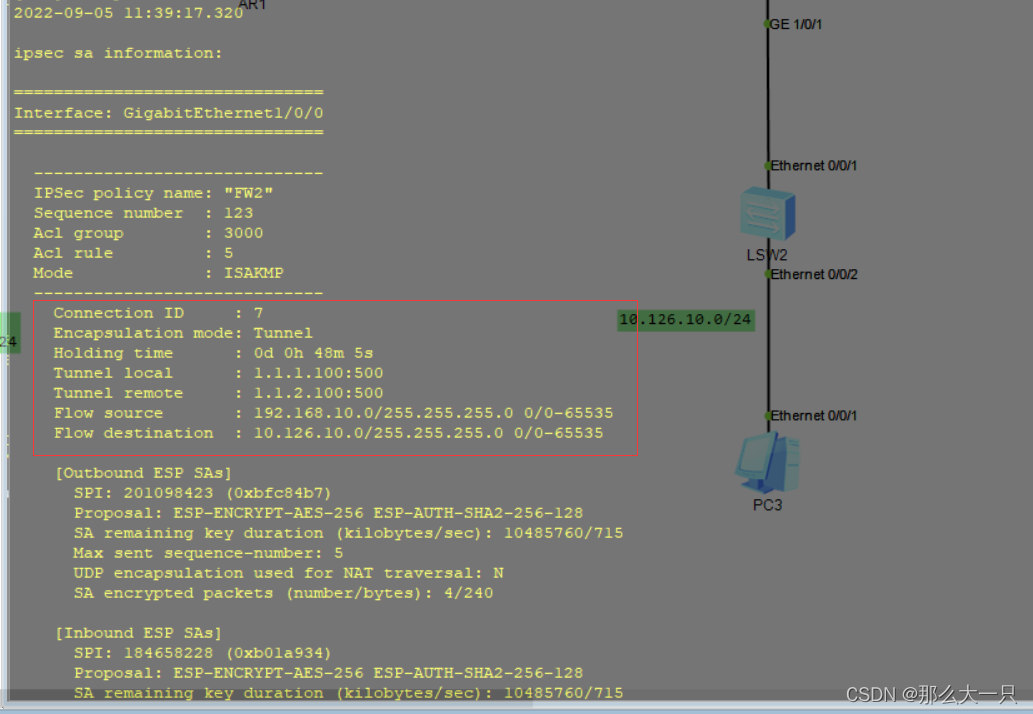
注意:后面需要让内网访问外网设置了nat需要设置旁路否则会导致无法连接 rule move 将策略nat往上移动 FW1: nat-policy rule name nat source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 source-address 192.168.20.0 mask 255.255.255.0 destination-address 10.126.10.0 mask 255.255.255.0 action no-nat rule name internet source-zone trust destination-zone untrust action source-nat easy-ip
FW2: nat-policy rule name nat source-zone trust destination-zone untrust source-address 10.126.10.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 destination-address 192.168.20.0 mask 255.255.255.0 action no-nat rule name internet source-zone trust destination-zone untrust action source-nat easy-ip
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4642.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
打赏
 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~

 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~休息一下~~


