https://hqyman.cn/post/4732.html 之前的H3C对接H3C、华为等设备的IPSEC
2个地区(假如没有固定IP都是拨号的情况下)需要通过中心节点中转相互访问
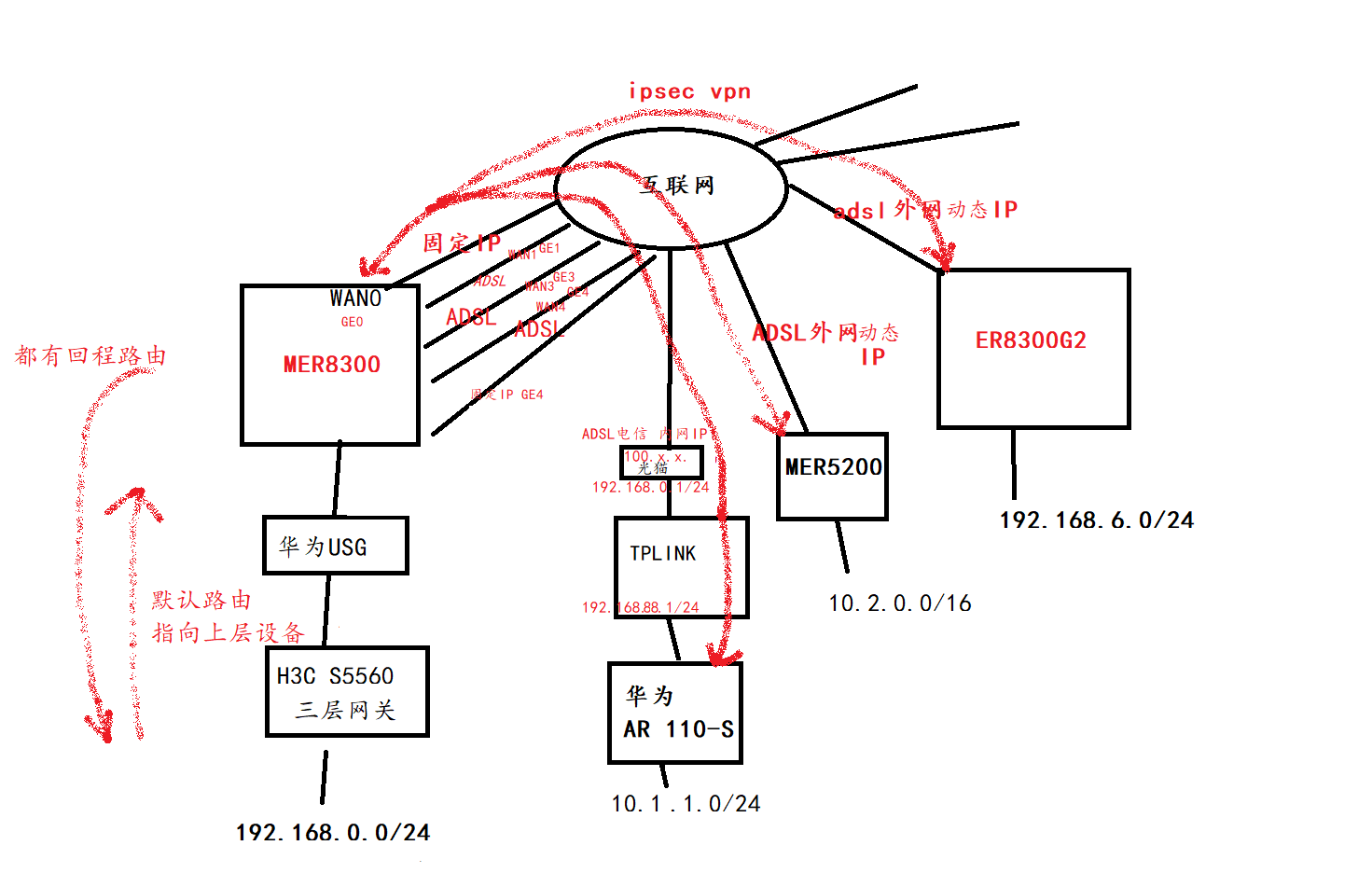
MER8300
#
ipsec policy-template WAN0(GE0) 1000
transform-set WAN0(GE0)@gz_branches
description WAN0(GE0)@gz_branches
ike-profile WAN0(GE0)@gz_branches
sa duration time-based 3600
sa duration traffic-based 1843200
// reverse-route dynamic 取消掉这动态路由
// reverse-route preference 50 取消掉这动态路由
acl number 3100
description no-nat-ipsecvpn
rule 2050 deny ip source 192.168.12.0 0.0.0.255 destination 10.2.0.0 0.0.255.255 //假如MER5200下的10.2.0.0/16要跟ER8300下的192.168.12.0/24通信,需要做deny并且成对的做
rule 2060 deny ip source 10.2.0.0 0.0.255.255 destination 192.168.12.0 0.0.0.255 //假如MER5200下的10.2.0.0/16要跟ER8300下的192.168.12.0/24通信,需要做deny并且成对的做
rule 60000 permit ip
//MER8300的兴趣流,是由对方发起,所以本地ACL兴趣流可以不用做
//取消动态注入路由的同时,需手工加入静态路由,否则转发会出错,因为本地策略路由只在VLAN1,分区进来不经过VLAN1,本地策略路由失效
ip route-static 10.1.0.0 16 ER8300固定IP地址网关 preference 50
MER5200
只管加兴趣流和DENY ACL就OK了
acl number 3100
description no-nat-ipsecvpn
rule 2000 deny ip source 10.2.0.0 0.0.255.255 destination 192.168.0.0 0.0.0.255 //跟中心
rule 2100 deny ip source 10.2.0.0 0.0.255.255 destination 192.168.212.0 0.0.0.255 //跟中心另外网段
rule 2200 deny ip source 10.2.0.0 0.0.255.255 destination 192.168.12.0 0.0.0.255 //跟分区
rule 60000 permit ip
#
acl advanced name WAN0(GE0)
rule 0 permit ip source 10.2.0.0 0.0.255.255 destination 192.168.212.0 0.0.0.255 //跟中心另外网段
rule 1 permit ip source 10.2.0.0 0.0.255.255 destination 192.168.0.0 0.0.0.255 //跟中心
rule 2 permit ip source 10.b.0.0 0.0.255.255 destination 192.168.12.0 0.0.0.255 //跟分区
AR-110S
模拟AR对接2个地方,一个用fqnd,一个用ip
acl number 3000 //deny nat acl
rule 5 deny ip source 10.1.1.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
rule 6 deny ip source 10.1.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 10 permit ip source 10.1.1.0 0.0.0.255
acl name b 3998 //分区到分区,通过IP模式
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
acl name A_B 3999 //中心到分区
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
#
ipsec proposal B
esp authentication-algorithm md5
esp encryption-algorithm 3des
#
ike proposal 2 // 注意,2和3 故意不一样 integrity-algorithm hmac-md5-96
encryption-algorithm 3des
dh group2
authentication-algorithm md5
authentication-method pre-share
integrity-algorithm hmac-md5-96
prf hmac-md5
ike proposal 3 // 注意,2和3 故意不一样,ntegrity-algorithm hmac-sha2-256 , prf hmac-sha2-256 这个不知道用途
encryption-algorithm 3des
dh group2
authentication-algorithm md5
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer B_C //分区去分区,用FQDN
undo version 2
exchange-mode aggressive
pre-shared-key cipher xxxxxx
ike-proposal 3
local-id-type fqdn // 可有可无,因为我们是用IP链接,remote-id-type ip 默认是这个,不显示出来
remote-id a.com //可有可无,因为我们是用IP链接
local-id b.com //可有可无,因为我们是用IP链接
dpd type periodic
remote-address ER8300外网固定IP
rsa encryption-padding oaep
rsa signature-padding pss
ikev2 authentication sign-hash sha2-256
ike peer A_B //去中心节点 ,用IP
undo version 2
exchange-mode aggressive
pre-shared-key cipher xxxxxxx
ike-proposal 2
local-id-type fqdn //本地链接类型,FQDN
remote-id-type fqdn //对端链接类型,FQDN
remote-id a.com //本地FQDN
local-id b.com //对端FQDN
dpd type periodic
remote-address 中心IP
rsa encryption-padding oaep
rsa signature-padding pss
ikev2 authentication sign-hash md5
#
ipsec policy A_B 1000 isakmp //去分区
security acl 3998
pfs dh-group1
ike-peer B_C
proposal B
route inject dynamic
ipsec policy A_B 2000 isakmp //去中心节点
security acl 3999
pfs dh-group1
ike-peer A_B
proposal B
route inject dynamic
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/4787.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~