测试拓扑更新

在 strongSwan测试环境的基础上,增加了一个“移动办公”的区域,使用一台win10虚拟机,模拟windows客户端连接到strongSwan VPN网关。
拓扑中增加的配置
增加的R-1路由器配置
# 接口和路由配置
interface GigabitEthernet0/0
ip address 192.168.40.254 255.255.255.0
ip nat inside
interface GigabitEthernet0/15
ip address 51.1.1.1 255.255.255.0
ip nat outside
ip route 0.0.0.0 0.0.0.0 51.1.1.254
# NAT配置
access-list 10 permit 192.168.40.0 0.0.0.255
ip nat inside source list 10 interface GigabitEthernet0/15 overload
# DHCP配置
ip dhcp pool client
network 192.168.40.0 255.255.255.0
default-router 192.168.40.254
dns-server 202.102.224.68Internet路由器增加配置
interface GigabitEthernet4
ip address 51.1.1.254 255.255.255.0
ip nat inside
ip access-list standard 10
......
40 permit 51.1.1.0 0.0.0.255
!测试目的
实现aliyun、hwcloud、tencloud三个站点的192.168.10.0/24、192.168.20.0/24、192.168.30.0/24的互相访问
移动办公可以通过aliyun站点访问192.168.10.0/24、192.168.20.0/24、192.168.30.0/24三个网段的服务。
配置思路
aliyun站点创建一个名为to-hwcloud的连接,用来与hwcloud站点建立ipsec隧道。 aliyun站点创建一个名为to-tencloud的连接,用来与tencloud站点建立ipsec隧道。
tencloud站点创建一个名为to-hwcloud的连接,用来与hwcloud站点建立ipsec连接。
aliyun站点创建一个名为rw-site的连接,用来接受 移动办公 站点的ipsec连接。
三个站点的网关路由器修改路由条目,分别将对方站点的路由指向本站点的strongswan主机。
主要配置
aliyun站点
aliyun站点创建了3个连接,其中to-hwlcoud用来与hwcloud站点建立ipsec连接;to-tencloud用来与tencloud站点建立ipsec连接。rw-site连接用来接受win10移动办公的远程接入。
与hwcloud站点和tencloud站点使用pubkey方式进行认证,使用strongswan默认的安全提议。 rw-site连接用来接受win10客户端移动办公的远程接入,使用eap-mschapv2方式进行扩展身份认证。
root@aliyun:~# cat /etc/swanctl/swanctl.conf # 连接配置
connections {
# 定义名为 to-hwcloud 的连接 to-hwcloud {
# 指定对端地址
remote_addrs = 13.1.1.2
# 本端认证方式
local {
# 指定认证方式为 pubkey
auth = pubkey
# 选择本端使用的服务器证书
certs = aliyunCert.pem
}
# 对端认证方式
remote {
# 指定认证方式为 pubkey
auth = pubkey
# 指定对端证书中的 altName
id = "C=CN, O=strongswan, CN=hwCloud.strongswan.local"
}
# 感兴趣流
children {
# 为连接 to-hwcloud`配置感兴趣流
to-hwlcoud {
local_ts = 192.168.10.0/24
remote_ts = 192.168.20.0/24
# 配置启动方式为 trap, 即流量触发隧道建立
start_action = trap
}
}
}
to-tencloud {
remote_addrs = 31.1.1.2
local {
auth = pubkey
certs = aliyunCert.pem
}
remote {
auth = pubkey
id = "C=CN,O=strongswan,CN=tenCloud.strongswan.local"
}
children {
to-tencloud {
local_ts = 192.168.10.0/24
remote_ts = 192.168.30.0/24
start_action = trap
}
}
}
# 创建一个名为`rw-site额连接
rw-site {
# 配置本端使用的地址
local_addrs = 192.168.10.253
# 给对端分配虚拟IP使用的地址池
pools = rw-site
# 配置本端认证方式
local {
# 指定本端认证方式 pubkey
auth = pubkey
# 指定本端使用的证书
certs = aliyunRsaCert.pem
# 配置本端id, 这个id必须是包含在怔住中的 altName 内。
id = aliyun.strongswan.local
}
# 配置对端认证方式
remote {
# 对端认证方式为 eap-mschapv2
auth = eap-mschapv2
# 对端eap_id为any, 因为不知道与对端id,所以配置为any,接受任意对端id
eap_id = %any
}
# 配置子网
children {
# 为rw-site连接指定隧道感兴趣流
rw-site {
# 配置本端网络。
local_ts = 192.168.10.0/24,192.168.20.0/24,192.168.30.0/24
}
}
# 为rw-site站点指定安全提议。
# win10 支持的最高的ikev2算法强度还没有 strongswan 默认支持最低的算法强度高。
proposals = 3des-aes128-aes192-aes256-sha1-sha256-sha384-modp1024
} } # 配置地址池
pools {
rw-site {
addrs = 10.10.1.0/24
dns = 202.102.224.68
} } # 配置身份验证信息secrets {
eap-win10 {
id = win10
secret = win10
} }tencloud站点
tencloud站点配置了2个连接,其中net-net用来与aliyun站点建立ipsec连接;to-hwcloud用来与hwcloud站点建立ipsec连接,使用pubkey方式认证,使用strongswan默认的安全提议。
root@TenCloud:~# cat /etc/swanctl/swanctl.conf connections {
net-net {
remote_addrs = 21.1.1.2
local {
auth = pubkey
certs = tenCloudCert.pem
}
remote {
auth = pubkey
id = "C=CN,O=strongswan,CN=aliyun.strongswan.local"
}
children {
net-net {
local_ts = 192.168.30.0/24
remote_ts = 192.168.10.0/24
start_action = trap
}
}
}
to-hwcloud {
remote_addrs = 13.1.1.2
local {
auth = pubkey
certs = tenCloudCert.pem
}
remote {
auth = pubkey
id="C=CN,O=strongswan,CN=hwCloud.strongswan.local"
}
children {
to-hwcloud {
local_ts = 192.168.30.0/24
remote_ts = 192.168.20.0/24
start_action = trap
}
}
} }hwcloud站点
hwcloud河站点配置了2个连接,其中net-net用来与aliyun站点建立ipsec连接;to-tencloud用来与tencloud它站点建立ipsec连接,使用pubkey方式认证,使用strongswan默认的安全提议。
root@hwCloud:~# cat /etc/swanctl/swanctl.conf connections {
net-net {
remote_addrs = 21.1.1.2
local {
auth = pubkey
certs = hwCloudCert.pem
}
remote {
auth = pubkey
id = "C=CN, O=strongswan, CN=aliyun.strongswan.local"
}
children {
net-net {
local_ts = 192.168.20.0/24
remote_ts = 192.168.10.0/24
start_action = trap
}
}
}
to-tencloud {
remote_addrs = 31.1.1.2
local {
auth = pubkey
certs = hwCloudCert.pem
}
remote {
auth = pubkey
id = "C=CN,O=strongswan,CN=tenCloud.strongswan.local"
}
children {
to-tencloud {
local_ts = 192.168.20.0/24
remote_ts = 192.168.30.0/24
start_action = trap
}
}
} }站点主机firewalld配置
各站点主机需要开启linux内核的ipv4转发功能
# 即时生效
sysctl -w net.ipv4.ip_forward=1
# 永久生效
vim /etc/sysctl.conf
net.ipv4.ip_forward=1需要注意masquerade功能,需要关闭。不然对端访问本端网络中其它主机的流量会被firewalld的masquerade功能给自动NAT了。
root@TenCloud:~# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens3
sources:
services: dhcpv6-client ssh
ports: 500/udp 4500/udp
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:网关路由器回指路由配置
三个网关路由器分别将对端的路由指向本端的strongSwan主机。
tencloud网关路由配置
ip route 192.168.10.0 255.255.255.0 192.168.30.253
ip route 192.168.20.0 255.255.255.0 192.168.30.253hwcloud网关路由配置
ip route 192.168.10.0 255.255.255.0 192.168.20.253
ip route 192.168.30.0 255.255.255.0 192.168.20.253aliyun网关路由配置
ip route 192.168.20.0 255.255.255.0 192.168.10.253
ip route 192.168.30.0 255.255.255.0 192.168.10.253win10主机路由配置
win10主机使用内置的ikev2建立隧道连接,不会根据协商报文中的children创建路由,这里需要手动在ikev2连接上添加路由
Add-VpnConnectionRoute -ConnectionName "strongswan" -DestinationPrefix "192.168.10.0/24" -PassThruAdd-VpnConnectionRoute -ConnectionName "strongswan" -DestinationPrefix "192.168.20.0/24" -PassThruAdd-VpnConnectionRoute -ConnectionName "strongswan" -DestinationPrefix "192.168.30.0/24" -PassThrualiyun站点nat转发win10主机数据配置
因为关闭了firewalld的masquerade功能,所以win10接入网络后访问192.168.10.254的流量被aliyun站点的主机直接转发出去了,源地址为配置文件中配置的虚拟IP地址。

为了方便win10终端的访问,减少三个站点的路由配置,这里给虚拟IP地址配置rich rule规则。
firewalld rich rule配置,将源地址为10.10.1.0/24的虚拟IP地址池中的地址流量使用masquerade地址伪装后转发出去。
firewall-cmd --permanent --zone=public --add-rich-rule='rule family=ipv4 source address=10.10.1.0/24 masquerade'firewall-cmd --reload
root@aliyun:~# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens3
sources:
services: dhcpv6-client ssh
ports: 500/udp 4500/udp 8080/tcp
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="10.10.1.0/24" masquerade
root@aliyun:~#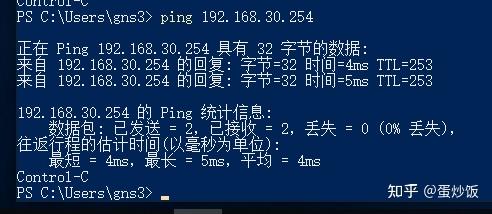
在aliyun站点的firewalld上配置了rich rule规则后,win10访问任意站点的数据,都被masquerade使用aliyun站点的主机地址转发出去了。
firewalld rich rule配置参考资料 https://www.sbarjatiya.com/notes_wiki/index.php/CentOS_8.x_firewalld_rich_rules#:~:text=Masquerading%20with%20Rich%20rules%20To%20check%20if%20IP,defined%20in%20the%20zone%20%E2%80%98testing%E2%80%99%20will%20be%20masqueraded
隧道状态
aliyun站点的隧道信息
root@aliyun:~# swanctl --list-sas
to-tencloud: #2, ESTABLISHED, IKEv2, 8483d10e950e0eac_i* b377ca7f00a54b9e_r
local 'C=CN, O=strongswan, CN=aliyun.strongswan.local' @ 192.168.10.253[4500]
remote 'C=CN, O=strongswan, CN=tenCloud.strongswan.local' @ 31.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1160s ago, rekeying in 12069s
to-tencloud: #4, reqid 2, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1160s ago, rekeying in 2149s, expires in 2800s
in cfa2a514, 168 bytes, 2 packets, 1158s ago
out c376553f, 168 bytes, 2 packets, 1158s ago
local 192.168.10.0/24
remote 192.168.30.0/24
to-hwcloud: #1, ESTABLISHED, IKEv2, bc9bc34fb668f6b7_i* 22081e5522b8723c_r
local 'C=CN, O=strongswan, CN=aliyun.strongswan.local' @ 192.168.10.253[4500]
remote 'C=CN, O=strongswan, CN=hwCloud.strongswan.local' @ 13.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1420s ago, rekeying in 12313s
to-hwlcoud: #3, reqid 1, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1421s ago, rekeying in 1978s, expires in 2540s
in c0aa9cd4, 168 bytes, 2 packets, 1418s ago
out ce72656d, 168 bytes, 2 packets, 1419s ago
local 192.168.10.0/24
remote 192.168.20.0/24root@aliyun:~# ip xfrm state
src 192.168.10.253 dst 31.1.1.2
proto esp spi 0xc376553f reqid 2 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0xb97edf34f6177434610063f833103fb66b9d6921 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x2, bitmap 0x00000000
src 31.1.1.2 dst 192.168.10.253
proto esp spi 0xcfa2a514 reqid 2 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0x2c9668bcd712b056af99b2fd6b091dbf240aaacd 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x2, oseq 0x0, bitmap 0x00000003
src 192.168.10.253 dst 13.1.1.2
proto esp spi 0xce72656d reqid 1 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x73a85a0b754b7cd738f1aabd4853f5a2a13a5cc0 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x2, bitmap 0x00000000
src 13.1.1.2 dst 192.168.10.253
proto esp spi 0xc0aa9cd4 reqid 1 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0x3ef2b0bce19a9d1a297856f832d6676a24caf5d3 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x2, oseq 0x0, bitmap 0x00000003tencloud站点的隧道信息
root@TenCloud:~# swanctl --list-sas
to-hwcloud: #2, ESTABLISHED, IKEv2, 67970b0e2d6d5f40_i* 1929ec4535961ada_r
local 'C=CN, O=strongswan, CN=tenCloud.strongswan.local' @ 192.168.30.253[4500]
remote 'C=CN, O=strongswan, CN=hwCloud.strongswan.local' @ 13.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1196s ago, rekeying in 11970s
to-hwcloud: #4, reqid 2, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1196s ago, rekeying in 2099s, expires in 2764s
in c611c421, 84 bytes, 1 packets, 1195s ago
out c87fdd13, 84 bytes, 1 packets, 1195s ago
local 192.168.30.0/24
remote 192.168.20.0/24
net-net: #1, ESTABLISHED, IKEv2, 8483d10e950e0eac_i b377ca7f00a54b9e_r*
local 'C=CN, O=strongswan, CN=tenCloud.strongswan.local' @ 192.168.30.253[4500]
remote 'C=CN, O=strongswan, CN=aliyun.strongswan.local' @ 21.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1203s ago, rekeying in 12681s
net-net: #3, reqid 1, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1203s ago, rekeying in 2139s, expires in 2757s
in c376553f, 168 bytes, 2 packets, 1201s ago
out cfa2a514, 168 bytes, 2 packets, 1201s ago
local 192.168.30.0/24
remote 192.168.10.0/24root@TenCloud:~# ip xfrm state
src 192.168.30.253 dst 13.1.1.2
proto esp spi 0xc87fdd13 reqid 2 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x7d188c9f8d2762603c74b29a7bf64028680fdc83 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x1, bitmap 0x00000000
src 13.1.1.2 dst 192.168.30.253
proto esp spi 0xc611c421 reqid 2 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0x2a6feb93527cefbe7a7f12d0fb1a8c9e4274ca20 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001
src 192.168.30.253 dst 21.1.1.2
proto esp spi 0xcfa2a514 reqid 1 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x2c9668bcd712b056af99b2fd6b091dbf240aaacd 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x2, bitmap 0x00000000
src 21.1.1.2 dst 192.168.30.253
proto esp spi 0xc376553f reqid 1 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0xb97edf34f6177434610063f833103fb66b9d6921 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x2, oseq 0x0, bitmap 0x00000003
root@TenCloud:~#hwcloud站点的隧道信息
root@hwCloud:~# swanctl --list-sas
to-tencloud: #2, ESTABLISHED, IKEv2, 67970b0e2d6d5f40_i 1929ec4535961ada_r*
local 'C=CN, O=strongswan, CN=hwCloud.strongswan.local' @ 192.168.20.253[4500]
remote 'C=CN, O=strongswan, CN=tenCloud.strongswan.local' @ 31.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1254s ago, rekeying in 12787s
to-tencloud: #4, reqid 2, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1254s ago, rekeying in 2209s, expires in 2706s
in c87fdd13, 84 bytes, 1 packets, 1253s ago
out c611c421, 84 bytes, 1 packets, 1253s ago
local 192.168.20.0/24
remote 192.168.30.0/24
net-net: #1, ESTABLISHED, IKEv2, bc9bc34fb668f6b7_i 22081e5522b8723c_r*
local 'C=CN, O=strongswan, CN=hwCloud.strongswan.local' @ 192.168.20.253[4500]
remote 'C=CN, O=strongswan, CN=aliyun.strongswan.local' @ 21.1.1.2[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
established 1522s ago, rekeying in 11490s
net-net: #3, reqid 1, INSTALLED, TUNNEL-in-UDP, ESP:AES_GCM_16-128
installed 1522s ago, rekeying in 1993s, expires in 2439s
in ce72656d, 168 bytes, 2 packets, 1519s ago
out c0aa9cd4, 168 bytes, 2 packets, 1520s ago
local 192.168.20.0/24
remote 192.168.10.0/24root@hwCloud:~# ip xfrm state
src 192.168.20.253 dst 31.1.1.2
proto esp spi 0xc611c421 reqid 2 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x2a6feb93527cefbe7a7f12d0fb1a8c9e4274ca20 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x1, bitmap 0x00000000
src 31.1.1.2 dst 192.168.20.253
proto esp spi 0xc87fdd13 reqid 2 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0x7d188c9f8d2762603c74b29a7bf64028680fdc83 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001
src 192.168.20.253 dst 21.1.1.2
proto esp spi 0xc0aa9cd4 reqid 1 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x3ef2b0bce19a9d1a297856f832d6676a24caf5d3 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x2, bitmap 0x00000000
src 21.1.1.2 dst 192.168.20.253
proto esp spi 0xce72656d reqid 1 mode tunnel
replay-window 32 flag af-unspec
aead rfc4106(gcm(aes)) 0x73a85a0b754b7cd738f1aabd4853f5a2a13a5cc0 128
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x2, oseq 0x0, bitmap 0x00000003
root@hwCloud:~#隧道建立过程site-to-site ikev2
这是一段完整的ikev2隧道建立过程的日志,使用pubkey认证方式,默认安全提议。
IKE_SA_INIT Request
收到来自21.1.1.2站点的IKE_SA_INIT请求。
06[NET] received packet: from 21.1.1.2[500] to 192.168.20.253[500] (1048 bytes)
06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP)
]
06[IKE] 21.1.1.2 is initiating an IKE_SA这是本端选择的IKE安全提议
06[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519根据NAT_S_IP和NAT_D_IP信息,在链路上至少卒存在2个NAT路由器。
06[IKE] local host is behind NAT, sending keep alives
06[IKE] remote host is behind NATIKE_SA_INIT Response
将ike_sa_init响应发送到对端。
06[IKE] sending cert request for "C=CN, O=strongSwan, CN=strongSwan Root CA--outform"
06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG)
N(CHDLESS_SUP) N(MULT_AUTH) ]
06[NET] sending packet: from 192.168.20.253[500] to 21.1.1.2[500] (273 bytes)IKE_AUTH Request
收到来自发起方的IKE_AUTH请求。
05[NET] received packet: from 21.1.1.2[4500] to 192.168.20.253[4500] (1040 bytes)
05[ENC] parsed IKE_AUTH request 1 [ IDi CERT N(INIT_CONTACT) CERTREQ IDr AUTH SA TSi TSr N(MOBIKE_SUP) N(NO_AD
D_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]收到strongswan root ca和1个未知ca的证书请求。接收到一个终端实体证书。
05[IKE] received cert request for "C=CN, O=strongSwan, CN=strongSwan Root CA--outform"
05[IKE] received 1 cert requests for an unknown ca
05[IKE] received end entity cert "C=CN, O=strongswan, CN=aliyun.strongswan.local"根据发起方的请求信息,查找匹配的对等配置,选择了net-net连接定义。
05[CFG] looking for peer configs matching 192.168.20.253[C=CN, O=strongswan, CN=hwCloud.strongswan.local]...21
.1.1.2[C=CN, O=strongswan, CN=aliyun.strongswan.local]
05[CFG] selected peer config 'net-net'IKE_AUTH_Response
检查证书状态
05[CFG] using trusted certificate "C=CN, O=strongswan, CN=aliyun.strongswan.local"
05[CFG] using trusted ca certificate "C=CN, O=strongSwan, CN=strongSwan Root CA--outform"
05[CFG] reached self-signed root ca with a path length of 0
05[CFG] checking certificate status of "C=CN, O=strongswan, CN=aliyun.strongswan.local"
05[CFG] certificate status is not available认证证书
05[IKE] authentication of 'C=CN, O=strongswan, CN=aliyun.strongswan.local' with ED25519 successful
05[IKE] peer supports MOBIKE
05[IKE] authentication of 'C=CN, O=strongswan, CN=hwCloud.strongswan.local' (myself) with ED25519 successful向对方发送本端的实体证书
05[IKE] sending end entity cert "C=CN, O=strongswan, CN=hwcloud.strongswan.local"建立IKE_SA
05[IKE] IKE_SA net-net[1] established between 192.168.20.253[C=CN, O=strongswan, CN=hwCloud.strongswan.local]...21.1.1.2[C=CN, O=strongswan, CN=aliyun.strongswan.local]
05[IKE] scheduling rekeying in 13012s
05[IKE] maximum IKE_SA lifetime 14452s选择esp加密安全提议
05[CFG] selected proposal: ESP:AES_GCM_16_128/NO_EXT_SEQ建立CHILD_SA,生成IKE_AUTH响应发送给对方。
05[IKE] CHILD_SA net-net{3} established with SPIs ce72656d_i c0aa9cd4_o and TS 192.168.20.0/24 === 192.168.10.0/24
05[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) ]
05[NET] sending packet: from 192.168.20.253[4500] to 21.1.1.2[4500] (752 bytes)测试
aliyun站点访问hwcloud站点
在aliyun站点ping测试访问hwloud站点的192.168.20.254
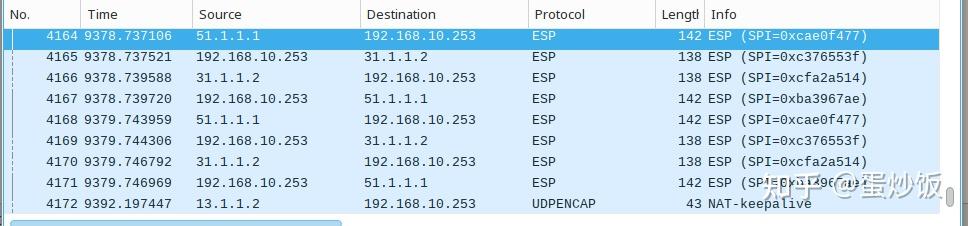
在aliyun站点处抓包,访问192.168.20.254的报文都被封装进了esp报文中
在hwcloud站点抓包,访问192.168.20.254的加密报文被hwcloud站点主机收到后,解密后修改原报文的MAC地址后明文转发给192.168.20.254,192.158.20.254返回的响应报文,hwcloud站点收到后,将其封装进esp报文后发给aliyun站点主机。
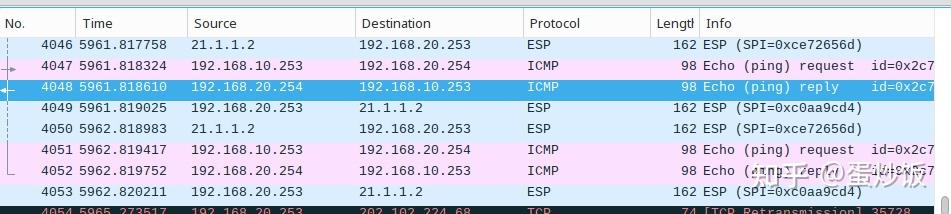
aliyun站点访问tencloud站点
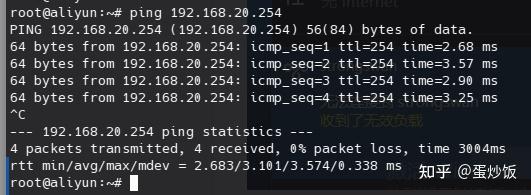
在aliyun站点ping测试访问hwloud站点的192.168.30.254

在aliyun站点处抓包,访问192.168.30.254的报文都被封装进了esp报文中
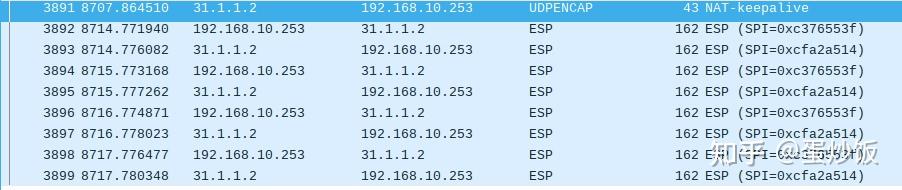
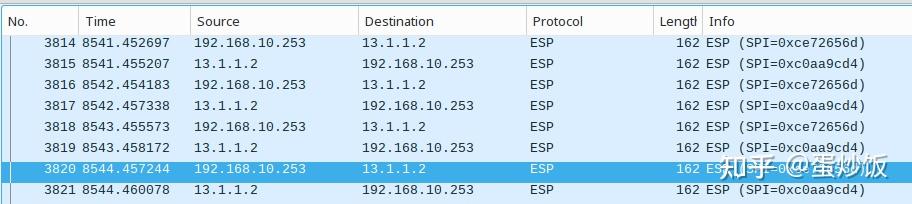
在tencloud它站点抓包,访问192.168.30.254的加密报文被tencloud站点主机收到后,解密后修改原报文的MAC地址后明文转发给192.168.30.254,192.158.30.254返回的响应报文,tencloud站点收到后,将其封装进esp报文后发给aliyun站点主机。
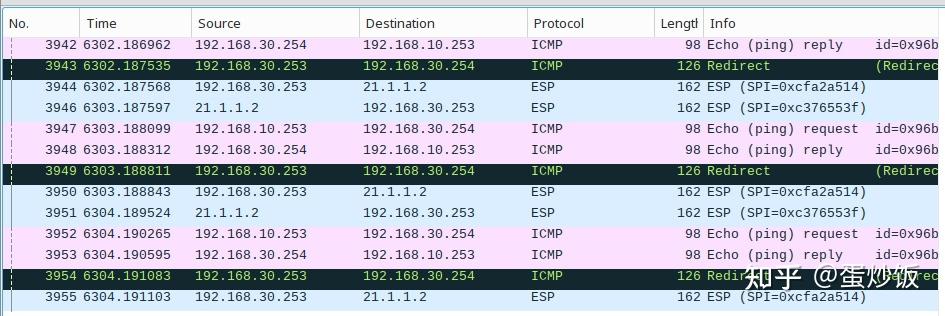
这里发现一个问题,每次tencloud站点每次收到192.168.30.254给aliyun站点192.168.10.253的响应报文后,总会给192.168.30.254发送一个icmp的重定向报文。原因未知。
问题处理
收到了无效载荷

ikev2协商日志
root@aliyun:~# swanctl --log
......
15[NET] received packet: from 51.1.1.1[4500] to 192.168.10.253[4500] (84 bytes)
15[ENC] parsed IKE_AUTH request 5 [ AUTH ]
15[IKE] authentication of '192.168.40.1' with EAP successful
15[IKE] authentication of 'aliyun.strongswan.local' (myself) with EAP
15[IKE] peer requested virtual IP %any
15[IKE] no virtual IP found for %any requested by 'win10'
15[IKE] peer requested virtual IP %any6
15[IKE] no virtual IP found for %any6 requested by 'win10'
15[IKE] no virtual IP found, sending INTERNAL_ADDRESS_FAILURE
15[IKE] IKE_SA rw-site[7] established between 192.168.10.253[aliyun.strongswan.local]...51.1.1.1[192.168.40.1]
15[IKE] scheduling rekeying in 13761s
15[IKE] maximum IKE_SA lifetime 15201s
15[IKE] configuration payload negotiation failed, no CHILD_SA built
15[IKE] failed to establish CHILD_SA, keeping IKE_SA
15[ENC] generating IKE_AUTH response 5 [ AUTH N(MOBIKE_SUP) N(NO_ADD_ADDR) N(INT_ADDR_FAIL) ]
15[NET] sending packet: from 192.168.10.253[4500] to 51.1.1.1[4500] (108 bytes)
07[NET] received packet: from 51.1.1.1[4500] to 192.168.10.253[4500] (68 bytes)
07[ENC] parsed INFORMATIONAL request 6 [ D ]
07[IKE] received DELETE for IKE_SA rw-site[7]
07[IKE] deleting IKE_SA rw-site[7] between 192.168.10.253[aliyun.strongswan.local]...51.1.1.1[192.168.40.1]
07[IKE] IKE_SA deleted
07[ENC] generating INFORMATIONAL response 6 [ ]
07[NET] sending packet: from 192.168.10.253[4500] to 51.1.1.1[4500] (60 bytes)
^Cdisconnecting...
root@aliyun:~#没有找到ipv4或ipv6地址池,导致CHILD_SA协商失败。
15[IKE] peer requested virtual IP %any
15[IKE] no virtual IP found for %any requested by 'win10'
15[IKE] peer requested virtual IP %any6
15[IKE] no virtual IP found for %any6 requested by 'win10'
15[IKE] no virtual IP found, sending INTERNAL_ADDRESS_FAILURE
......
15[IKE] configuration payload negotiation failed, no CHILD_SA built
15[IKE] failed to establish CHILD_SA, keeping IKE_SA检查/etc/swanctl/swanctl.conf配置
......# 配置地址池
pool {
rw-site {
addrs = 10.10.1.0/24
dns = 202.102.224.68
} } ......地址池配置中pool少了个s
......# 配置地址池
# pool { 修改为 pools {pools {
rw-site {
addrs = 10.10.1.0/24
dns = 202.102.224.68
} } ......修改后隧道建立成功
root@aliyun:~# swanctl --list-sas
rw-site: #9, ESTABLISHED, IKEv2, baaa72758aecd45d_i f7ed0993de042405_r*
local 'aliyun.strongswan.local' @ 192.168.10.253[4500]
remote '192.168.40.1' @ 51.1.1.1[4500] EAP: 'win10' [10.10.1.1]
3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
established 202s ago, rekeying in 14073s
rw-site: #7, reqid 3, INSTALLED, TUNNEL-in-UDP, ESP:AES_CBC-256/HMAC_SHA1_96
installed 202s ago, rekeying in 3082s, expires in 3758s
in c536f4db, 60 bytes, 1 packets, 195s ago
out d425f504, 0 bytes, 0 packets
local 192.168.10.0/24 192.168.20.0/24 192.168.30.0/24
remote 10.10.1.1/32
......
root@aliyun:~#
root@aliyun:~# ip xfrm state
src 192.168.10.253 dst 51.1.1.1
proto esp spi 0xd425f504 reqid 3 mode tunnel
replay-window 0 flag af-unspec
auth-trunc hmac(sha1) 0xbb3286f287d3a65468b71c92551b7ec0ff111eb0 96
enc cbc(aes) 0x8dda899338418aca7a2420b471c7118d6c075581bf55b02702dfd2fb25cd6ef1
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x0, oseq 0x0, bitmap 0x00000000
src 51.1.1.1 dst 192.168.10.253
proto esp spi 0xc536f4db reqid 3 mode tunnel
replay-window 32 flag af-unspec
auth-trunc hmac(sha1) 0x57453af88e9beeaa1142506fb4745bae69699522 96
enc cbc(aes) 0x50cad1b1ae4ba5ffacbbdbdbd9aff3f49eb45ffa996d6e80e5ae3a9e38cf4359
encap type espinudp sport 4500 dport 4500 addr 0.0.0.0
anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001
......
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://hqyman.cn/post/8615.html 非本站原创文章欢迎转载,原创文章需保留本站地址!
休息一下~~



 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~